华为USG防火墙搭建IPsecVPN
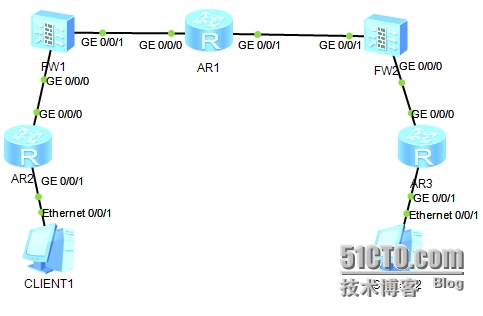
1.实验拓扑:
使用模拟器eNSP(版本号:1.2.00.350 V100R002c00)+AR3260+USG5500
AR1模拟运营商
2.实验需求:
a) 在FW1上做PAT,让C1可以上互联网
b) 在FW1和FW2之间做IPsecVPN,让C1、C2间实现私网通信
3.实验步骤:
a) IP地址规划:
FW1 | GE0/0/0 |
| AR1 | GE0/0/0 |
|
GE0/0/1 |
| GE0/0/1 |
| ||
FW2 | GE0/0/0 |
| AR2 | GE0/0/0 |
|
GE0/0/1 |
| GE0/0/1 |
| ||
AR3 | GE0/0/0 |
| C1 |
| |
GE0/0/1 |
| C2 |
|
b) 配置脚本如下:
FW1
<SRG>sy //进入系统视图
[SRG]sysnameFW1 //修改设备名称
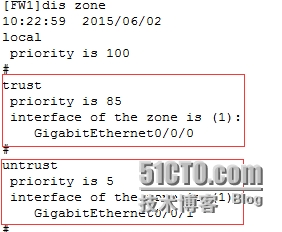
[FW1]firewallzone trust //进入trust区域
[FW1-zone-trust]addint g0/0/0 //把g0/0/0接口加入到trust区域中
[FW1-zone-trust]q //退出到上一层模式
[FW1]firewallzone untrust
[FW1-zone-untrust]addint g0/0/1
[FW1-zone-untrust]intg0/0/0 //进入接口视图
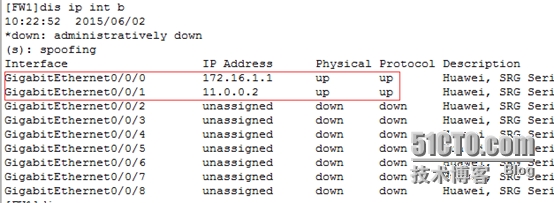
[FW1-GigabitEthernet0/0/0]ipadd 172.16.1.1 24 //配置IP地址
[FW1-GigabitEthernet0/0/0]intg0/0/1
[FW1-GigabitEthernet0/0/1]ipadd 11.0.0.2 24
[FW1]dis zone //查看区域
[FW1]disip int b //查看接口IP地址
AR1
<Huawei>sy
[Huawei]sysnameAR1
[AR1]intg0/0/0
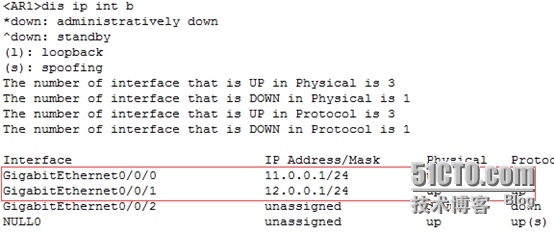
[AR1-GigabitEthernet0/0/0]ipadd 11.0.0.1 24
[AR1-GigabitEthernet0/0/0]intg0/0/1
[AR1-GigabitEthernet0/0/1]ipadd 12.0.0.1 24
<AR1>disip int b
FW2
<SRG>sy
[SRG]sysnameFW2
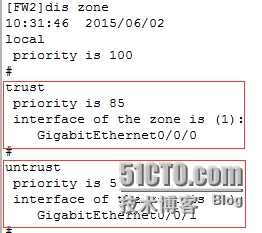
[FW2]firewallzone trust
[FW2-zone-trust]addint g0/0/0
[FW2-zone-trust]q
[FW2]firewallzone untrust
[FW2-zone-untrust]addint g0/0/1
[FW2-zone-untrust]intg0/0/0
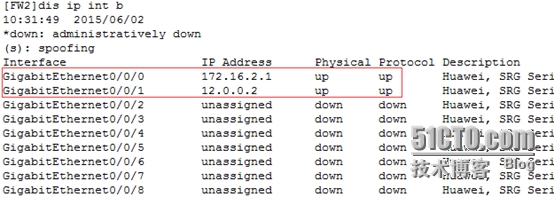
[FW2-GigabitEthernet0/0/0]ipadd 172.16.2.1 24
[FW2-GigabitEthernet0/0/0]intg0/0/1
[FW2-GigabitEthernet0/0/1]ipadd 12.0.0.2 24
[FW2]diszone
[FW2]disip int b
AR2
<Huawei>sy
[Huawei]sysnameAR2
[AR2]intg0/0/0
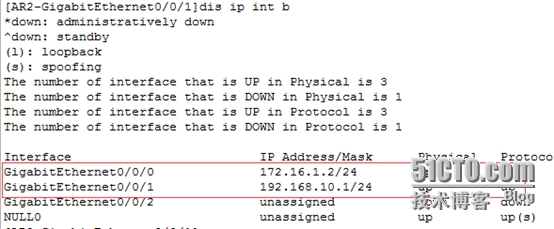
[AR2-GigabitEthernet0/0/0]ipadd 172.16.1.2 24
[AR2-GigabitEthernet0/0/0]intg0/0/1
[AR2-GigabitEthernet0/0/1]ip add 192.168.10.1 24
[AR2-GigabitEthernet0/0/1]disip int b
AR3
<Huawei>sy
[Huawei]sysnameAR3
[AR3]intg0/0/0
[AR3-GigabitEthernet0/0/0]ipadd 172.16.2.2 24
[AR3-GigabitEthernet0/0/0]intg0/0/1
[AR3-GigabitEthernet0/0/1]ipadd 192.168.20.1 24
[AR3-GigabitEthernet0/0/1]disip int b
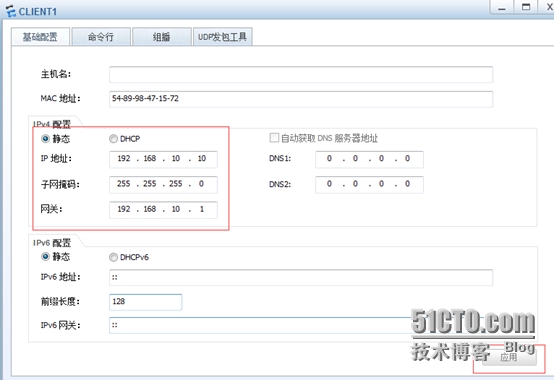
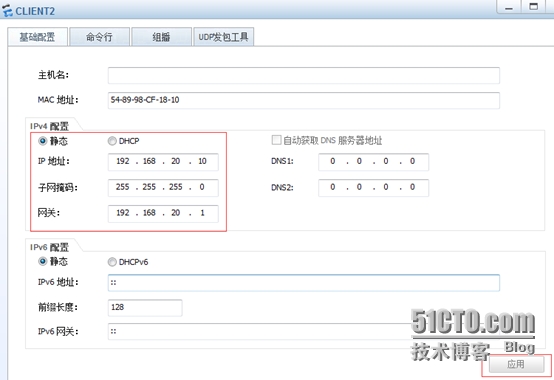
C1
C2
-----------------------以上是IP地址配置-------------------------
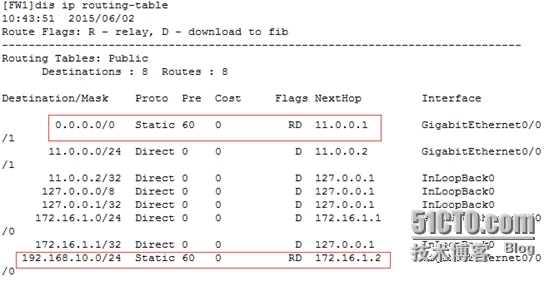
FW1
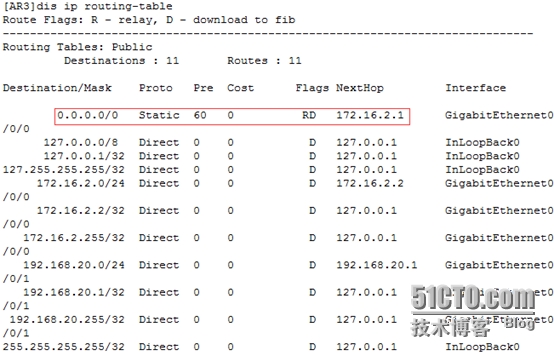
[FW1]iproute-static 0.0.0.0 0 11.0.0.1 //出口做默认路由
[FW1]iproute-static 192.168.10.0 24 172.16.1.2 //向下指静态路由
[FW1]disip routing-table //查看路由表
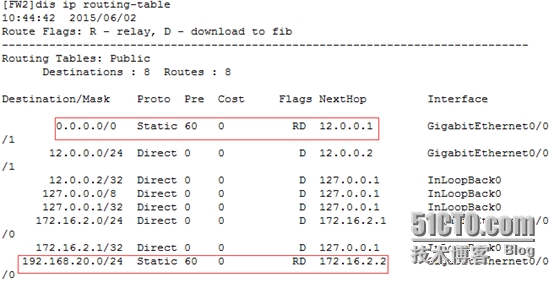
FW2
[FW2]iproute-static 0.0.0.0 0 12.0.0.1
[FW2]iproute-static 192.168.20.0 24 172.16.2.2
[FW2]disip routing-table
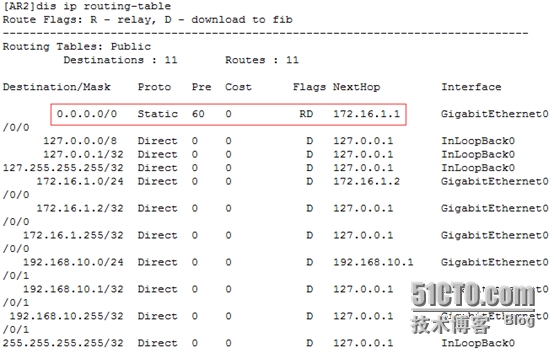
AR2
[AR2]iproute-static 0.0.0.0 0 172.16.1.1
[AR2]disip routing-table
AR3
[AR3]iproute-static 0.0.0.0 0 172.16.2.1
[AR3]disip routing-table
--------------------一上是路由配置--------------------------
FW1
[FW1]nat-policyinterzone trust untrust outbound //进入域间NAT策略视图
[FW1-nat-policy-interzone-trust-untrust-outbound-1]policy source 192.168.10.0mask 24 //创建NAT策略并进入策略视图
[FW1-nat-policy-interzone-trust-untrust-outbound-1]actionsource-nat //指定需匹配流量的源地址
[FW1-nat-policy-interzone-trust-untrust-outbound-1]easy-ipg0/0/1 //直接使用接口IP作为转换地址
因为防火墙默认拒绝ICMP流量通过,所以需要做以下配置
[FW1]policyinterzone trust untrust outbound //进入域间的outbound方向
[FW1-policy-interzone-trust-untrust-outbound]policy1 //创建转发策略
[FW1-policy-interzone-trust-untrust-outbound-1]policy source 192.168.10.0mask 24 //当源是这个网段的时
[FW1-policy-interzone-trust-untrust-outbound-1]actionpermit //允许通过
测试C1上互联网
---------------------以上是PAT配置---------------------
FW1
[FW1]acl3001
[FW1-acl-adv-3001]rule permit ip source 192.168.10.0 0.0.0.255 destination192.168.20.0 0.0.0.255 //配置感兴趣流
[FW1-acl-adv-3001]ikeproposal 1 //创建IKE安全提议,并进入IKE安全提议视图
[FW1-ike-proposal-1]encryption-algorithmaes-cbc //配置加密算法
[FW1-ike-proposal-1]authentication-methodpre-share //配置认证方法
[FW1-ike-proposal-1]authentication-algorithmsha1 //配置认证算法
[FW1-ike-proposal-1]dhgroup2 //配置DH组标识
[FW1-ike-proposal-1]ikepeer a //创建IKE Peer,并进入IKE Peer视图
[FW1-ike-peer-a]ike-proposal1 //引用已配置的IKE安全提议
[FW1-ike-peer-a]pre-shared-keyabc123 //配置预共享密钥认证,abc123是秘钥
[FW1-ike-peer-a]remote-address12.0.0.2 //指定对端发起IKE协商的地址
[FW1-ike-peer-a]ipsecproposal tran1 //创建安全提议,并进入安全提议视图
[FW1-ipsec-proposal-tran1]transformesp //配置传送数据时采用的安全协议
[FW1-ipsec-proposal-tran1]espauthentication-algorithm sha1 //配置ESP方式采用的认证算法
[FW1-ipsec-proposal-tran1]espencryption-algorithm aes //配置ESP协议使用的加密算法
[FW1-ipsec-proposal-tran1]ipsecpolicy map1 10 isakmp //创建安全策略,并进入安全策略视图
[FW1-ipsec-policy-isakmp-map1-10]securityacl 3001 //在安全策略中引用已创建的感兴趣流
[FW1-ipsec-policy-isakmp-map1-10]proposaltran1 //在安全策略中引用已创建的安全提议
[FW1-ipsec-policy-isakmp-map1-10]ike-peera //在安全策略中引用IKE Peer
[FW1-ipsec-policy-isakmp-map1-10]intg0/0/1
[FW1-GigabitEthernet0/0/1]ipsecpolicy map1 //把安全策略应用到出口
FW2
[FW2]acl3001
[FW2-acl-adv-3001]rule permit ip source 192.168.20.0 0.0.0.255 destination192.168.10.0 0.0.0.255
[FW2-ike-proposal-1]encryption-algorithmaes-cbc
[FW2-ike-proposal-1]authentication-methodpre-share
[FW2-ike-proposal-1]authentication-algorithmsha1
[FW2-ike-proposal-1]dhgroup2
[FW2-ike-proposal-1]ikepeer a
[FW2-ike-peer-a]pre-shared-keyabc123
[FW2-ike-peer-a]remote-address11.0.0.2
[FW2-ike-peer-a]ipsecproposal tran1
[FW2-ipsec-proposal-tran1]transformesp
[FW2-ipsec-proposal-tran1]espauthentication-algorithm sha1
[FW2-ipsec-proposal-tran1]espencryption-algorithm aes
[FW2-ipsec-proposal-tran1]ipsecpolicy map1 10 isakmp
[FW2-ipsec-policy-isakmp-map1-10]securityacl 3001
[FW2-ipsec-policy-isakmp-map1-10]proposaltran1
[FW2-ipsec-policy-isakmp-map1-10]ike-peera
[FW2-ipsec-policy-isakmp-map1-10]intg0/0/1
[FW2-GigabitEthernet0/0/1]ipsecpolicy map1
--------------------以上是IPsec VPN配置-------------------
FW1
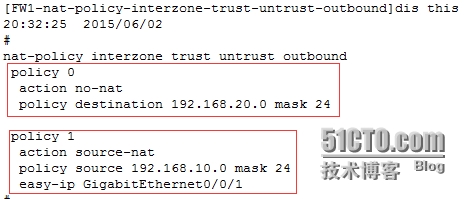
[FW1]nat-policyinterzone trust untrust outbound //进入域间的outbound方向
[FW1-nat-policy-interzone-trust-untrust-outbound]policy0 //创建转发策略
[FW1-nat-policy-interzone-trust-untrust-outbound-0]policydestination 192.168.20.0 mask 24 //当目标是这个网段时
[FW1-nat-policy-interzone-trust-untrust-outbound-0]actionno-nat //不被NAT
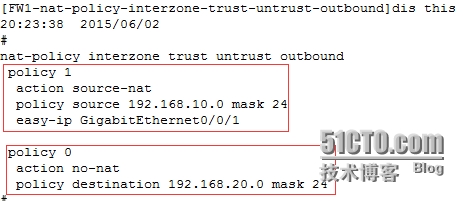
因为NAT策略优先级是从前往后依次执行的,所以需要把不被NAT的策略调到前面
[FW1-nat-policy-interzone-trust-untrust-outbound]policymove 0 before 1 //将policy 0优先级调整到policy 1的前面
-----------------以上是感兴趣流出去时不被NAT---------------
FW1
因为防火墙默认拒绝ICMP流量通过,所以需要做以下配置
[FW1]policyinterzone local untrust inbound //进入域间的inbound方向
[FW1-policy-interzone-local-untrust-inbound]policy 0 //创建转发策略
[FW1-policy-interzone-local-untrust-inbound-0]policysource 12.0.0.2 0 //当源是这个主机时
[FW1-policy-interzone-local-untrust-inbound-0]actionpermit //允许通过
FW2
[FW2]policyinterzone local untrust inbound
[FW2-policy-interzone-local-untrust-inbound]policy1
[FW2-policy-interzone-local-untrust-inbound-1]policysource 11.0.0.2 0
[FW2-policy-interzone-local-untrust-inbound-1]actionpermit
测试建立IPsecVPN的两端是否可以通信
因为建立IPsecVPN需要两端可以正常通信,所以需要做以上配置
-----------------以上是配置两端防火墙可以正常通信---------------
FW2
[FW2]policyinterzone trust untrust outbound
[FW2-policy-interzone-trust-untrust-outbound]policy1
[FW2-policy-interzone-trust-untrust-outbound-1]policy source 192.168.20.0mask 24
[FW2-policy-interzone-trust-untrust-outbound-1]actionpermit
----------------以上是配置允许C2这边流量可以出去-----------------
[FW1]policyinterzone trust untrust inbound //进入域间的inbound方向
[FW1-policy-interzone-trust-untrust-inbound]policy1
[FW1-policy-interzone-trust-untrust-inbound-1]policysource 192.168.20.0 mask 24
[FW1-policy-interzone-trust-untrust-inbound-1]policydestination 192.168.10.0 mask 24
[FW1-policy-interzone-trust-untrust-inbound-1]actionpermit
FW2
[FW2]policyinterzone trust untrust inbound
[FW2-policy-interzone-trust-untrust-inbound]policy1
[FW2-policy-interzone-trust-untrust-inbound-1]policysource 192.168.10.0 mask 24
[FW2-policy-interzone-trust-untrust-inbound-1]policydestination 192.168.20.0 mask 24
[FW2-policy-interzone-trust-untrust-inbound-1]actionpermit
------------------以上是配置允许流量可以进------------------
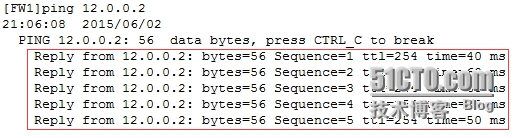
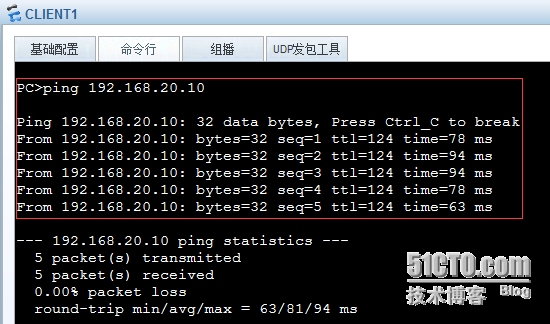
4.验证结果:
验证C1与C2之间私网通信
本文出自 “波仔网络技术” 博客,请务必保留此出处http://bozai666.blog.51cto.com/10138815/1657664
郑重声明:本站内容如果来自互联网及其他传播媒体,其版权均属原媒体及文章作者所有。转载目的在于传递更多信息及用于网络分享,并不代表本站赞同其观点和对其真实性负责,也不构成任何其他建议。




![TJ]AK4{L9@XQ_R(]SFXEQCQ.png 技术分享](http://s3.51cto.com/wyfs02/M02/6D/DF/wKiom1VtuDbSdaDrAAJSIA6aOZo258.jpg)


































