NAT对IPSec VPN的影响
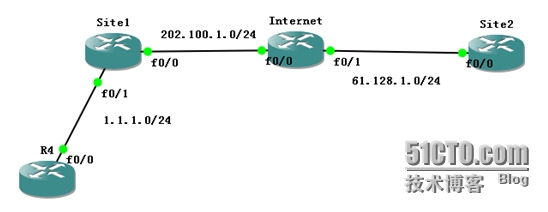
Site1和Site2建立IPSec VPN,Site1做NAT,怎样解决NAT对IPsec VPN的影响,有以下解决方案.
1. Site1与Site2建立IPSec VPN:
Site1:
crypto isakmp policy 100
encr3des
authentication pre-share
group2
crypto isakmp key cisco address 61.128.1.1
ip access-list extended vpn
permit ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255
crypto ipsec transform-set myset esp-3desesp-sha-hmac
crypto map ccie 10 ipsec-isakmp
setpeer 61.128.1.1
settransform-set myset
matchaddress vpn
interface FastEthernet0/0
ipaddress 202.100.1.1 255.255.255.0
crypto map ccie
interface FastEthernet0/1
ipaddress 1.1.1.10 255.255.255.0
ip route 0.0.0.0 0.0.0.0 202.100.1.10
Site2:
crypto isakmp policy 100
encr3des
authentication pre-share
group2
crypto isakmp key cisco address 202.100.1.1
ip access-list extended vpn
permit ip 2.2.2.0 0.0.0.255 1.1.1.0 0.0.0.255
crypto ipsec transform-set myset esp-3des esp-sha-hmac
crypto map ccie 10 ipsec-isakmp
setpeer 202.100.1.1
settransform-set myset
matchaddress vpn
interface FastEthernet0/0
ipaddress 61.128.1.1 255.255.255.0
crypto map ccie
interface lo0
ipaddress 2.2.2.2 255.255.255.0
ip route 0.0.0.0 0.0.0.0 61.128.1.10
Internet:
interface FastEthernet0/0
ipaddress 202.100.1.10 255.255.255.0
no shutdown
interface FastEthernet0/1
ipaddress 61.128.1.10 255.255.255.0
noshutdown
测试:
Site2#ping 1.1.1.1 source lo0
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 1.1.1.1, timeout is 2 seconds:
Packet sent with a source address of 2.2.2.2
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max= 68/81/104 ms
Site2#show crypto isakmp sa
IPv4 Crypto ISAKMP SA
dst src state conn-id slot status
61.128.1.1 202.100.1.1 QM_IDLE 1001 0 ACTIVE
Site2#show crypto engine connections active
Crypto Engine Connections
ID Interface Type Algorithm Encrypt Decrypt IP-Address
3 Fa0/0 IPsec 3DES+SHA 0 4 61.128.1.1
4 Fa0/0 IPsec 3DES+SHA 4 0 61.128.1.1
1002 Fa0/0 IKE SHA+3DES 0 0 61.128.1.1
IPSec VPN建立成功,流量加密。
在Site1 上做NAT,查看情况:
Site1(config)#ip access-listextended PAT
Site1(config-ext-nacl)#permitip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255
Site1(config)#ip nat insidesource list PAT interface f0/0 overload
Site1(config)#int f0/0
Site1(config-if)#ip natoutside
Site1(config)#int f0/1
Site1(config-if)#ip nat inside
发现:
R4#ping 2.2.2.2
Type escape sequence toabort.
Sending 5, 100-byte ICMPEchos to 2.2.2.2, timeout is 2 seconds:
U.U.U
Success rate is 0 percent(0/5)
*Mar 1 00:24:30.035:ICMP: dst (1.1.1.1) host unreachable rcv from 202.100.1.10.U
*Mar 1 00:24:32.071:ICMP: dst (1.1.1.1) host unreachable rcv from 202.100.1.10.U
Site1#show ip nattranslations
Pro Inside global Inside local Outside local Outside global
icmp 202.100.1.1:3 1.1.1.1:3 2.2.2.2:3 2.2.2.2:3
发现U.U.U,因为感兴趣流不匹配,被转换了,没有加密发送到internet,目的IP为2.2.2.2的数据包抵达internet,因为internet没有去往2.2.2.2的路由,所以为源回送host unreachable信息,该如何解决?
第一种解决方案:
Site1:扩展ACL
ip access-list extended PAT
deny ip 1.1.1.0 0.0.0.255 2.2.2.0 0.0.0.255
permit ip 1.1.1.0 0.0.0.255 any
(deny 掉感兴趣流,让感兴趣流不转换)
注意:要在deny前面加5,要是不加的话就去后面了,要先把它deny掉,在转换。是不是发现此刻没有 转换了吧。可以加密了吧,因为感兴趣流出现了。
第二种解决方案:
Site1:标准ACL
Interfaceloopback 100
Ip address10.10.10.10 255.255.255.0
Access-list1 permit 1.1.1.0 0.0.0.255
route-maptest
match ip address 1
set interface loopback100
int f0/1
ip policy route-map test
exit
这个时候匹配感兴趣流了,送到这个环回口上去,环回口随便写个地址。
环回口是出去还可以回来的,回来后再从这个外部接口F0/0出去了,就加密了。
要实现nat就要满足3个条件:感兴趣流(满足),inside接口进,outside接口出(不满足)。
这时必须还要在加一台路由器,所以我加了R4,因为我之前做的是用环回口1.1.1.1,自身发起的流量,这个自身的流量route-map是控制不了的。一定要让这个流量从某一个物理接口进入,我这个策略才好使。
本文出自 “优乐美” 博客,请务必保留此出处http://youlemei.blog.51cto.com/2294538/1653913
郑重声明:本站内容如果来自互联网及其他传播媒体,其版权均属原媒体及文章作者所有。转载目的在于传递更多信息及用于网络分享,并不代表本站赞同其观点和对其真实性负责,也不构成任何其他建议。