Linux SNAT/DNAT设置
背景及原理分析
现有组网
外网(即公司大网):10.0.0.0/8
内网(即实验室网络):108.28.194.0/24
网络改造
打通内网和外网有以下几种方法:
内网主机直接连接到外网:网络简单,但改造成本太大
VPN:每台外网主机访问内网时都需要设置VPN
NAT:仅需内网增加网关主机同时连接内外网即可,其他主机无需修改。
本文采用NAT的方案:用一台具备多网卡的Linux服务器作为内网网关,本次实践采用SBCX服务器,其网络配置如下:
内网网卡为eth3,地址为108.28.194.1/24
外网网卡为eth4,地址为10.92.244.141-145/24,网关为10.92.244.1
PS:外网地址10.92.2444.141用来转发一般内网主机与外网通信的数据包;10.92.244.142-145用为映射到内网的某些主机上,以便外网主机可以主动访问内网主机。
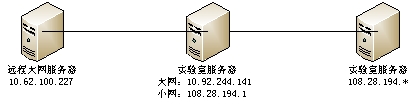
实验室网访问大网
内网网关只需要打开路由转发功能,并设置iptables SNAT规则转发内网数据包:
iptables -t nat -A POSTROUTING -s 108.28.194.0/24 -o eth4 -j SNAT --to-source 10.92.244.141
或者采用IP地址伪装的方式
iptables -t nat -A POSTROUTING -s 108.28.194.0/24-o eth4 -j MASQUERADE
这样仅能解决内网主机主动去访问外网主机的场景。
大网访问实验室网
大网主动访问实验室主机时有两种情况:特定端口或不定端口。
访问特定主机特定端口:这种场景一般用于对外提供某项服务如FTP服务/WEB服务等,将服务器放置在内网中可以有效的保护该服务器不被攻击,而通过网关来转发外网的正常的服务器请求。
示例: 108.28.194.5对外提供FTP服务,只需要在网关计算机上增加如下规则
iptables -t nat -A PREROUTING -d 10.92.244.141 p tcp dport 21 -j DNAT --to-destination 108.28.194.41:80
外网主机访问10.92.244.141:21,实际上访问的是由内网主机108.28.194.5提供的FTP服务,其数据包走向及处理过程

注:S表示报文源地址源端口;D表示报文目的地址目的端口;红色表示文头部发生变化。
访问特定主机,但端口不固定:此时需要在内网网关主机上增加多个大网地址,并设置iptable规则将其中某个外网地址映射到某台内网主机上。如访问108.28.194.41这台主机,对应的外网地址为10.92.244.142,则需要在网关主机上增加如下规则
iptables -t nat -A POSTROUTING -s 108.28.194.41 -o eth4 -j SNAT --to-source 10.92.244.142
ptables -t nat -A PREROUTING -d 10.92.244.142 -j DNAT --to-destination 108.28.194.41
数据包走向及处理过程
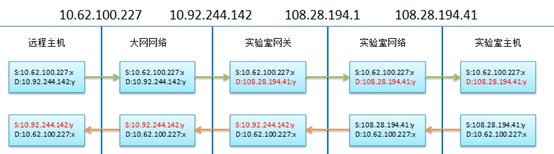
此时,在外网看来,内网主机108.28.194.41好像增加了大网地址10.92.244.142,但实际上该地址是加载到内网网关这台主机上,只是该主机将所有收到的、目的地址为10.92.244.142的数据包,将目的地址修
改为108.28.194.41并通过内网网卡转发到内网主机108.28.194.41上。
1 操作及验证
要求:
所有内网主机均可(主动)访问外网
外网主机可以通过10.92.244.142访问内网IP地址为108.28.194.41的主机
1.1 内网网管设置
查看IP地址设置,其中eth3连接实验室网络,eth4连接公司大网
[root@XABSC1 ~]# ifconfig
eth3 Link encap:Ethernet HWaddr 00:19:C6:3F:36:1E
inet addr:108.28.194.1 Bcast:108.28.194.255 Mask:255.255.255.0
inet6 addr: fe80::219:c6ff:fe3f:361e/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:198515 errors:0dropped:0 overruns:0 frame:0
TX packets:27542 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:14324965 (13.6 MiB) TXbytes:4552430 (4.3 MiB)
Base address:0x8800 Memory:fe180000-fe1a0000
eth4 Link encap:Ethernet HWaddr00:19:C6:3F:36:1F
inet addr:10.92.244.141 Bcast:10.92.244.255 Mask:255.255.255.0
inet6 addr: fe80::219:c6ff:fe3f:361f/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:27244 errors:0 dropped:0 overruns:0 frame:0
TX packets:30601 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:3053721 (2.9 MiB) TXbytes:2410105 (2.2 MiB)
Base address:0x8c00 Memory:fe1e0000-fe200000
eth4:0 Link encap:Ethernet HWaddr00:19:C6:3F:36:1F
inet addr:10.92.244.142 Bcast:10.92.244.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
Base address:0x8c00 Memory:fe1e0000-fe200000
打开内核转发并设置永久生效
[root@XABSC1 ~]# sed -i s/^net.ipv4.ip_forward.*/net.ipv4.ip_forward=1/g /etc/sysctl.conf
[root@XABSC1 ~]# sysctl –p
开启iptables服务并设置开机自动运行
[root@XABSC1 ~]# /etc/init.d/iptables start
清除防火墙规则: [ 确定 ]
把 chains 设置为 ACCEPT 策略:nat filter [ 确定 ]
正在卸载 Iiptables 模块: [ 确定 ]
应用 iptables 防火墙规则: [ 确定 ]
[root@XABSC1 ~]# chkconfig iptables on
[root@XABSC1 ~]# chkconfig --listiptables
iptables 0:off 1:off 2:on 3:on 4:on 5:on 6:off
[root@XABSC1 ~]#
清空规则:
[root@XABSC1 ~]# iptables -t filter -F
[root@XABSC1 ~]# iptables -t nat -F
设置iptables:
因为iptables处理报文时按照规则顺序依次匹配,所以要优先处理特殊IP(主机)
[root@XABSC1 ~]# iptables -t nat -APOSTROUTING -s 108.28.194.41 -o eth4 -jSNAT --to-source 10.92.244.142
[root@XABSC1 ~]# iptables -t nat -APREROUTING -d 10.92.244.142 -j DNAT --to-destination 108.28.194.41
转发实验室网络所有主机访问公司大网请求
[root@XABSC1 ~]# iptables -t nat -APOSTROUTING -s 108.28.194.0/255.255.255.0 -o eth4 -j MASQUERADE
保存iptables设置
[root@XABSC1 ~]# service iptables save
将当前规则保存到 /etc/sysconfig/iptables: [ 确定 ]
[root@XABSC1 ~]#
1.2 内网主机设置
只需要设置内网计算机网关指向Linux网关即可,或者仅设置访问公司大网时指向Linux网关
[root@sbcx230 ~]# route add default gw108.28.194.1
[root@sbcx230 ~]# route -nv
Kernel IP routing table
Destination Gateway Genmask Flags Metric Ref Use Iface
108.28.194.0 0.0.0.0 255.255.255.0 U 0 0 0 eth3
108.28.0.0 0.0.0.0 255.255.0.0 U 0 0 0 eth3
129.0.0.0 0.0.0.0 255.255.0.0 U 0 0 0 eth6
169.254.0.0 0.0.0.0 255.255.0.0 U 0 0 0 eth6
139.0.0.0 0.0.0.0 255.255.0.0 U 0 0 0 eth4
0.0.0.0 108.28.194.1 0.0.0.0 UG 0 0 0 eth3
[root@sbcx230 ~]#
1.3 网络连通性测试-内网访问外网(SNAT)
实验室主机IP配置,该主机没有在网关没有映射大网地址,因此在外网看到该主机的大网地址其实是网关的大网地址10.92.244.141
[root@gsbcx005_L ~]# ifconfig eth3
eth3 Link encap:Ethernet HWaddr00:19:C6:40:1A:B8
inet addr:108.28.194.5 Bcast:108.28.194.255 Mask:255.255.255.0
inet6 addr: fe80::219:c6ff:fe40:1ab8/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:204719 errors:0 dropped:0 overruns:0 frame:0
TX packets:106477 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:13647558 (13.0 MiB) TXbytes:6710314 (6.3 MiB)
通过内网主机ping外网主机
[root@gsbcx005_L ~]# ping -c 110.62.100.227
PING 10.62.100.227 (10.62.100.227) 56(84)bytes of data.
64 bytes from 10.62.100.227: icmp_seq=0ttl=53 time=31.0 ms
--- 10.62.100.227 ping statistics ---
1 packets transmitted, 1 received, 0% packetloss, time 0ms
rtt min/avg/max/mdev =31.096/31.096/31.096/0.000 ms, pipe 2
[root@gsbcx005_L ~]#
内网主机通过tcpdump分析对应网卡的数据包情况,显示ping 请求的源地址为108.28.194.5,目标地址为10.62.100.227
[root@gsbcx005_L ~]# tcpdump -i eth3 -vnnicmp
tcpdump: listening on eth3, link-type EN10MB(Ethernet), capture size 96 bytes
09:16:04.980731 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto 1,length: 84) 108.28.194.5 > 10.62.100.227: icmp 64: echo request seq 0
09:16:05.011792 IP (tos 0x14, ttl 53, id 45973, offset 0, flags [none], proto1, length: 84) 10.62.100.227 > 108.28.194.5: icmp 64: echo reply seq 0
网关主机通过tcpdump分析内网网卡的数据包情况,显示ping 请求的源地址为108.28.194.5,目标地址为10.62.100.227
[root@XABSC1 ~]# tcpdump -i eth3 -vnn icmp
tcpdump: listening on eth3, link-type EN10MB(Ethernet), capture size 96 bytes
08:50:39.992425 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto 1,length: 84) 108.28.194.5 > 10.62.100.227: icmp 64: echo request seq 0
08:50:40.023260 IP (tos 0x14, ttl 53, id 45973, offset 0, flags [none], proto1, length: 84) 10.62.100.227 > 108.28.194.5: icmp 64: echo reply seq 0
网关主机通过tcpdump分析外网网卡的数据包情况,显示ping 请求的源地址已被修改为10.92.244.141,但目标地址仍为10.62.100.227
[root@XABSC1 ~]# tcpdump -i eth4 -vnn icmp
tcpdump: listening on eth4, link-type EN10MB(Ethernet), capture size 96 bytes
08:50:39.992422 IP (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto 1,length: 84) 10.92.244.141 > 10.62.100.227: icmp 64: echo request seq 0
08:50:40.023238 IP (tos 0x14, ttl 54, id 45973, offset 0, flags [none], proto1, length: 84) 10.62.100.227 > 10.92.244.141: icmp 64: echo reply seq 0
外网主机通过tcpdump分析对应网卡的数据包情况,显示ping 请求的源地址改为10.92.244.141,但目标地址仍为10.62.100.227
[root@A23102876 ~]# tcpdump -i eth0 -vnn icmp
tcpdump: listening on eth0, link-type EN10MB(Ethernet), capture size 65535 bytes
09:18:42.846565 IP (tos 0x14, ttl 53, id 0,offset 0, flags [DF], proto ICMP (1), length 84)
10.92.244.141 > 10.62.100.227: ICMP echo request, id 34079, seq 0,length 64
09:18:42.846615 IP (tos 0x14, ttl 64, id45973, offset 0, flags [none], proto ICMP (1), length 84)
10.62.100.227 > 10.92.244.141: ICMP echo reply, id 34079, seq 0,length 64
外网主机通过10.92.244.141连接的是内网网关这台主机,无法主动访问内网被保护的主机108.28.194.5
[root@A23102876 ~]# ssh 10.92.244.141
[email protected]‘s password:
Last login: Mon Mar 16 08:29:56 2015 from108.28.194.104
[root@XABSC1 ~]# ifconfig
eth3 Link encap:Ethernet HWaddr00:19:C6:3F:36:1E
inet addr:108.28.194.1 Bcast:108.28.194.255 Mask:255.255.255.0
inet6 addr: fe80::219:c6ff:fe3f:361e/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:41311 errors:0 dropped:0 overruns:0 frame:0
TX packets:1736 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:2965404 (2.8 MiB) TXbytes:168190 (164.2 KiB)
Base address:0x8800 Memory:fe180000-fe1a0000
eth4 Link encap:Ethernet HWaddr00:19:C6:3F:36:1F
inet addr:10.92.244.141 Bcast:10.92.244.255 Mask:255.255.255.0
inet6 addr: fe80::219:c6ff:fe3f:361f/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:5079 errors:0 dropped:0 overruns:0 frame:0
TX packets:16294 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:628064 (613.3 KiB) TXbytes:1281684 (1.2 MiB)
Base address:0x8c00 Memory:fe1e0000-fe200000
eth4:0 Link encap:Ethernet HWaddr00:19:C6:3F:36:1F
inet addr:10.92.244.142 Bcast:10.92.244.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
Base address:0x8c00 Memory:fe1e0000-fe200000
eth4:1 Link encap:Ethernet HWaddr00:19:C6:3F:36:1F
inet addr:10.92.244.143 Bcast:10.92.244.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
Base address:0x8c00 Memory:fe1e0000-fe200000
eth4:2 Link encap:Ethernet HWaddr00:19:C6:3F:36:1F
inet addr:10.92.244.144 Bcast:10.92.244.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
Base address:0x8c00 Memory:fe1e0000-fe200000
eth4:3 Link encap:Ethernet HWaddr00:19:C6:3F:36:1F
inet addr:10.92.244.145 Bcast:10.92.244.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
Base address:0x8c00 Memory:fe1e0000-fe200000
eth4:4 Link encap:Ethernet HWaddr00:19:C6:3F:36:1F
inet addr:10.92.244.146 Bcast:10.92.244.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
Base address:0x8c00 Memory:fe1e0000-fe200000
eth4:5 Link encap:Ethernet HWaddr00:19:C6:3F:36:1F
inet addr:10.92.244.147 Bcast:10.92.244.255 Mask:255.255.255.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
Base address:0x8c00 Memory:fe1e0000-fe200000
eth6 Link encap:Ethernet HWaddr00:19:C6:3F:36:21
inet addr:108.58.0.1 Bcast:108.58.255.255 Mask:255.255.0.0
inet6 addr: fe80::219:c6ff:fe3f:3621/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:4480 errors:0 dropped:0 overruns:0 frame:0
TX packets:145 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:355590 (347.2 KiB) TXbytes:14405 (14.0 KiB)
Base address:0x9c00 Memory:fe3e0000-fe400000
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:2787 errors:0 dropped:0 overruns:0 frame:0
TX packets:2787 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:3664940 (3.4 MiB) TXbytes:3664940 (3.4 MiB)
1.4 网络连通性测试-外网访问内网(SNAT+DNAT)
实验室主机IP配置,该主机在网关上被映射的大网地址是10.92.244.142,因此在外网看到该主机的大网地址就是10.92.244.142
[root@sbcx230 ~]# ifconfig eth3
eth3 Link encap:Ethernet HWaddr00:19:C6:40:64:4A
inet addr:108.28.194.41 Bcast:108.28.194.255 Mask:255.255.255.0
inet6 addr: fe80::219:c6ff:fe40:644a/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:189085 errors:0 dropped:0 overruns:0 frame:0
TX packets:11598 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:12413224 (11.8 MiB) TX bytes:2205580 (2.1 MiB)
[root@sbcx230 ~]#
通过内网主机ping外网主机
[root@sbcx230 ~]# ping -c 1 10.62.100.227
PING 10.62.100.227 (10.62.100.227) 56(84)bytes of data.
64 bytes from 10.62.100.227: icmp_seq=0ttl=53 time=30.9 ms
--- 10.62.100.227 ping statistics ---
1 packets transmitted, 1 received, 0% packetloss, time 0ms
rtt min/avg/max/mdev =30.963/30.963/30.963/0.000 ms, pipe 2
[root@sbcx230 ~]#
内网主机通过tcpdump分析对应网卡的数据包情况,显示ping 请求的源地址为108.28.194.41,目标地址为10.62.100.227
[root@sbcx230 ~]# tcpdump -i eth3 -vnn icmp
tcpdump: listening on eth3, link-type EN10MB(Ethernet), capture size 96 bytes
09:04:58.593485 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto 1,length: 84) 108.28.194.41 > 10.62.100.227: icmp 64: echo request seq 0
09:04:58.624392 IP (tos 0x14, ttl 53, id 24403, offset 0, flags [none], proto1, length: 84) 10.62.100.227 > 108.28.194.41: icmp 64: echo reply seq 0
网关主机通过tcpdump分析内网网卡的数据包情况,显示ping 请求的源地址为108.28.194.41,目标地址为10.62.100.227
[root@XABSC1 ~]# tcpdump -i eth3 -vnn icmp
tcpdump: listening on eth3, link-type EN10MB(Ethernet), capture size 96 bytes
08:46:04.222468 IP (tos 0x0, ttl 64, id 0, offset 0, flags [DF], proto 1,length: 84) 108.28.194.41 > 10.62.100.227: icmp 64: echo request seq 0
08:46:04.253060 IP (tos 0x14, ttl 53, id 24403, offset 0, flags [none], proto1, length: 84) 10.62.100.227 > 108.28.194.41: icmp 64: echo reply seq 0
网关主机通过tcpdump分析外网网卡的数据包情况,显示ping 请求的源地址已被修改为10.92.244.142,但目标地址仍为10.62.100.227
[root@XABSC1 ~]# tcpdump -i eth4 -vnn icmp
tcpdump: listening on eth4, link-type EN10MB(Ethernet), capture size 96 bytes
08:46:04.222462 IP (tos 0x0, ttl 63, id 0, offset 0, flags [DF], proto 1,length: 84) 10.92.244.142 > 10.62.100.227: icmp 64: echo request seq 0
08:46:04.253035 IP (tos 0x14, ttl 54, id 24403, offset 0, flags [none], proto1, length: 84) 10.62.100.227 > 10.92.244.142: icmp 64: echo reply seq 0
外网主机通过tcpdump分析对应网卡的数据包情况,显示ping 请求的源地址改为10.92.244.142,但目标地址仍为10.62.100.227
[root@A23102876 ~]# tcpdump -i eth0 -vnn icmp
tcpdump: listening on eth0, link-type EN10MB(Ethernet), capture size 65535 bytes
09:14:07.069958 IP (tos 0x14, ttl 53, id 0,offset 0, flags [DF], proto ICMP (1), length 84)
10.92.244.142 > 10.62.100.227: ICMP echo request, id 47892, seq 0,length 64
09:14:07.070003 IP (tos 0x14, ttl 64, id24403, offset 0, flags [none], proto ICMP (1), length 84)
10.62.100.227 > 10.92.244.142: ICMP echo reply, id 47892, seq 0,length 64
外网主机通过10.92.244.142可以连接到内网主机上,并且通过ifcofnig命令查看发现内网主机确实没有10.92.244.142这个地址
[root@A23102876 ~]# ssh 10.92.244.142
[email protected]‘s password:
Last login: Sat Mar 14 10:44:29 2015 from10.62.100.227
-bash: [: missing `]‘
[root@sbcx230 ~]# ifconfig
eth3 Link encap:Ethernet HWaddr00:19:C6:40:64:4A
inet addr:108.28.194.41 Bcast:108.28.194.255 Mask:255.255.255.0
inet6 addr: fe80::219:c6ff:fe40:644a/64 Scope:Link
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
RX packets:264305 errors:0 dropped:0 overruns:0 frame:0
TX packets:11752 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:100
RX bytes:17370917 (16.5 MiB) TXbytes:2224099 (2.1 MiB)
eth3:1 Link encap:Ethernet HWaddr00:19:C6:40:64:4A
inet addr:108.28.194.42 Bcast:108.28.255.255 Mask:255.255.0.0
UP BROADCAST RUNNING MULTICAST MTU:1500 Metric:1
eth4 Link encap:Ethernet HWaddr00:19:C6:40:64:4B
inet addr:139.0.0.5 Bcast:139.0.255.255 Mask:255.255.0.0
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 b) TX bytes:0(0.0 b)
eth4:1 Link encap:Ethernet HWaddr00:19:C6:40:64:4B
inet addr:139.0.0.6 Bcast:139.0.255.255 Mask:255.255.0.0
UP BROADCAST MULTICAST MTU:1500 Metric:1
eth6 Link encap:Ethernet HWaddr00:19:C6:40:64:4D
inet addr:129.0.31.5 Bcast:129.0.255.255 Mask:255.255.0.0
UP BROADCAST MULTICAST MTU:1500 Metric:1
RX packets:0 errors:0 dropped:0 overruns:0 frame:0
TX packets:0 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:1000
RX bytes:0 (0.0 b) TX bytes:0(0.0 b)
lo Link encap:Local Loopback
inet addr:127.0.0.1 Mask:255.0.0.0
inet6 addr: ::1/128 Scope:Host
UP LOOPBACK RUNNING MTU:16436 Metric:1
RX packets:6757 errors:0 dropped:0 overruns:0 frame:0
TX packets:6757 errors:0 dropped:0 overruns:0 carrier:0
collisions:0 txqueuelen:0
RX bytes:5333716 (5.0 MiB) TXbytes:5333716 (5.0 MiB)
[root@sbcx230 ~]#
郑重声明:本站内容如果来自互联网及其他传播媒体,其版权均属原媒体及文章作者所有。转载目的在于传递更多信息及用于网络分享,并不代表本站赞同其观点和对其真实性负责,也不构成任何其他建议。




































