Linux安全管理-Iptables-NAT技术应用
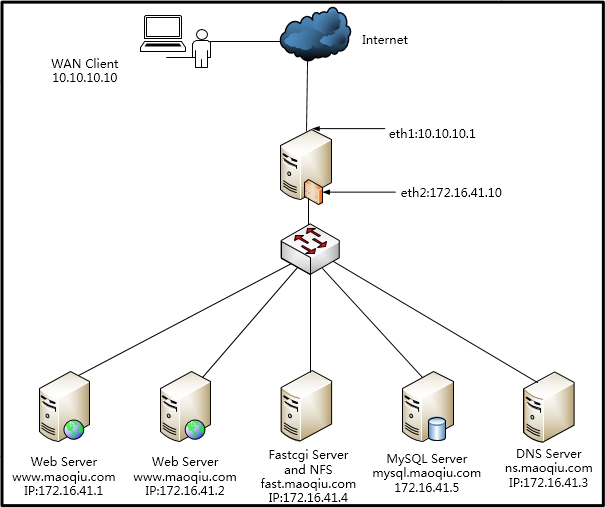
此文是对前面博文《 Linux网络服务-LAMP之基于NFS+Fastcgi的LAMP搭建 》的延伸,在外网与内网之间加了一台Linux网关服务器;
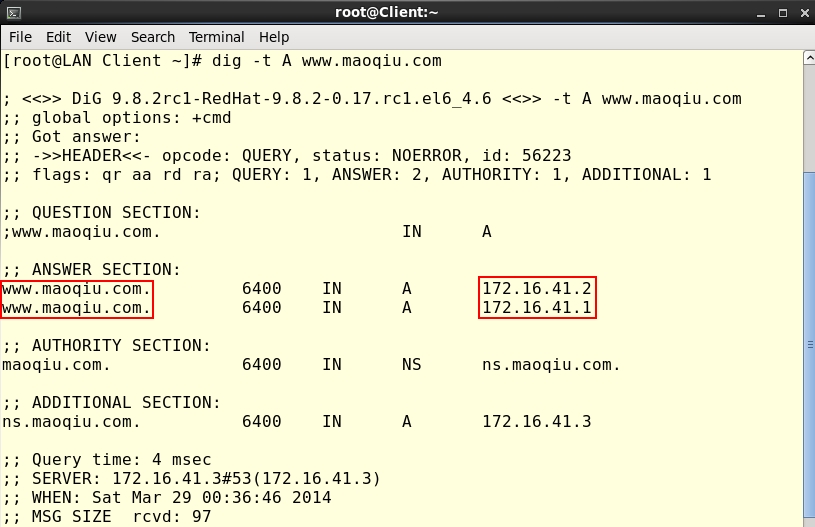
[root@ns ~]# vim /etc/named.conf
options {
directory "/var/named";
dump-file "/var/named/data/cache_dump.db";
statistics-file "/var/named/data/named_stats.txt";
allow-query { any; };
recursion yes;
rrset-order { class IN type A name "www.maoqiu.com" order cyclic; };
};
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
include "/etc/named.rfc1912.zones";[root@ns ~]# vim /etc/named.rfc1912.zones
acl LAN { #定义的ACL
172.16.0.0/16;
};
view LAN { #针对我内网网段内的用户对应的解析
match-clients { LAN; }; #凡是匹配到ACL中的条目都通过这个视图中的区域数据文件进行解析
zone "." IN {
type hint;
file "named.ca";
};
zone "localhost.localdomain" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "localhost" IN {
type master;
file "named.localhost";
allow-update { none; };
};
zone "1.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.0.ip6.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "1.0.0.127.in-addr.arpa" IN {
type master;
file "named.loopback";
allow-update { none; };
};
zone "0.in-addr.arpa" IN {
type master;
file "named.empty";
allow-update { none; };
};
zone "maoqiu.com" IN {
type master;
file "maoqiu.com.zone.lan";
};
zone "41.16.172.in-addr.arpa" IN {
type master;
file "172.16.41.zone.lan";
};
};
view wan { #针对除了我内网网段内的用户对应的解析
match-clients { any; };
zone "maoqiu.com" IN {
type master;
file "maoqiu.com.zone.wan";
};
};
#注意,对于内网区域数据文件一定要将其他区域数据文件包含在View中,根区域也不例外,对于外网客户我这里只做一个区域文件即可(3)创建正向和方向的区域数据文件:[root@ns ~]# cd /var/named/
#编辑针对内网服务器两台Web Server的正向区域数据文件
[root@ns named]# vim maoqiu.com.zone.lan
$TTL 6400
@ IN SOA ns.maoqiu.com. admin.maoqiu.com (
2014032701 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
IN NS ns
ns IN A 172.16.41.3
www IN A 172.16.41.1
www IN A 172.16.41.2
#编辑针对内网服务器两台Web Server的反向区域数据文件
[root@ns named]# vim 172.16.41.zone.lan
$TTL 6400
@ IN SOA ns.maoqiu.com. admin.maoqiu.com (
2014032701 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
IN NS ns.maoqiu.com.
3 IN PTR ns.maoqiu.com.
1 IN PTR www.maoqiu.com.
2 IN PTR www.maoqiu.com.
#编辑针对WAN Clients来访问时需要解析的区域数据文件
[root@ns named]# vim maoqiu.com.zone.wan
$TTL 6400
@ IN SOA ns.maoqiu.com. admin.maoqiu.com (
2014032701 ; serial
1D ; refresh
1H ; retry
1W ; expire
3H ) ; minimum
IN NS ns
ns IN A 172.16.41.3
www IN A 10.10.10.1[root@ns named]# chmod 640 maoqiu.com.zone.* 172.16.41.zone.lan [root@ns named]# chown root:named maoqiu.com.zone.* 172.16.41.zone.lan
[root@FireWall ~]# iptables -t nat -A PREROUTING -d 10.10.10.1 -p tcp --dport 80 -j DNAT --to-destination 172.16.41.1 [root@FireWall ~]# iptables -t nat -A PREROUTING -d 10.10.10.1 -p tcp --dport 80 -j DNAT --to-destination 172.16.41.2
[root@FireWall ~]#iptables -t nat -A PREROUTING -d 10.10.10.1 -p tcp --dport 53 -j DNAT --to-destination 172.16.41.3 [root@FireWall ~]#iptables -t nat -A PREROUTING -d 10.10.10.1 -p udp --dport 53 -j DNAT --to-destination 172.16.41.3
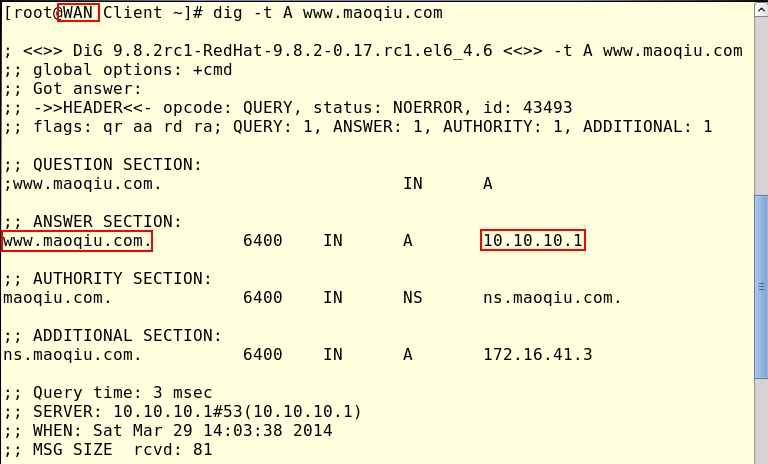
2.在本实验中主要重点就是DNS的解析配置以及Iptables的配置
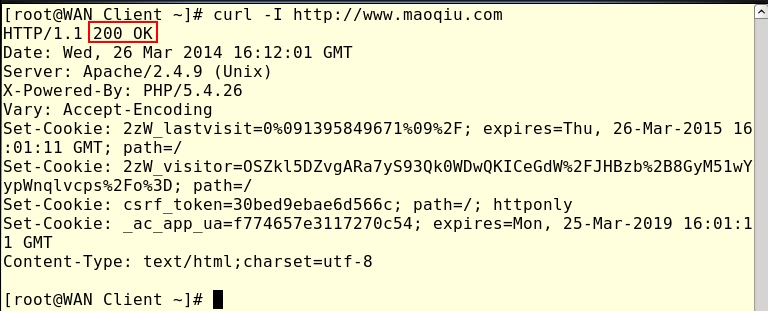
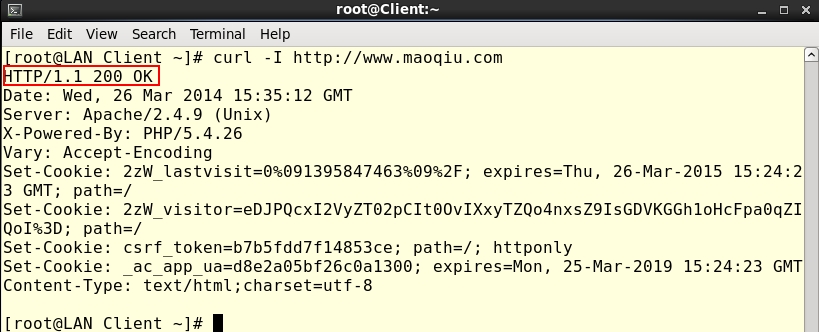
3.实验过程中,由于两台Web Server和DNS Server没有指定Linux网关即使服务器端收到了请求,但是在响应时却找不到回应目标,故服务器的Gateway要指向Linux网关服务器内网卡地址,Web Server的DNS要指向DNS Server!WAN Clients无需指定其网关,但是DNS需要指定!
本文出自 “一叶知秋” 博客,请务必保留此出处http://maoqiu.blog.51cto.com/8570467/1386888
郑重声明:本站内容如果来自互联网及其他传播媒体,其版权均属原媒体及文章作者所有。转载目的在于传递更多信息及用于网络分享,并不代表本站赞同其观点和对其真实性负责,也不构成任何其他建议。