zabbix应用之low-level discovery监控mysql
当一台服务器上MySQL有多个实例的时候,MySQL占用多个不同端口。利用zabbix的low-level discovery可以轻松监控。
思路参考:http://dl528888.blog.51cto.com/2382721/1357713
下面我写了一个简单的脚本,用于一键部署mysql监控。
一、客户端
在被监控端运行此脚本,前提条件已经安装好了zabbix agent(推荐yum安装)。脚本已在CentOS6.2 x86_64环境下测试通过。脚本在附件提供下载。
#!/bin/sh
#
# Filename: autoMonitorMysql.sh
# Revision: 1.0
# Date: 2014/08/12
# Author: Qicheng
# Email:
# Website: http://qicheng0211.blog.51cto.com/
# Description: zabbix low level discovery监控MySQL
# Notes: 在被监控客户端运行此脚本,前提条件已经安装好zabbix agent
#
ROOT_UID=0
if [ "$UID" -ne "$ROOT_UID" ];then
echo "Error: 必须以root用户运行此程序!"
exit 1
fi
AGENT_CONF="/etc/zabbix/zabbix_agentd.conf"
mkdir -p /etc/zabbix/monitor_scripts
# 创建 mysql low-level discovery 脚本
cat > /etc/zabbix/monitor_scripts/mysql_port_discovery.sh << ‘EOF‘
#!/bin/bash
#Function: mysql low-level discovery
#Script_name: mysql_port_discovery.sh
mysql() {
port=(`sudo /bin/netstat -tpln | awk -F "[ :]+" ‘BEGIN {IGNORECASE=1; } /mysql/ && /0.0.0.0/ {print $5}‘`)
max_index=$[${#port[@]}-1]
printf ‘{\n‘
printf ‘\t"data":[‘
for key in `seq -s‘ ‘ 0 $max_index`
do
printf ‘\n\t\t{‘
printf "\"{#MYSQLPORT}\":\"${port[${key}]}\"}"
if [ $key -ne $max_index ];then
printf ","
fi
done
printf ‘\n\t]\n‘
printf ‘}\n‘
}
$1
EOF
chown -R zabbix:zabbix /etc/zabbix/monitor_scripts
chmod +x /etc/zabbix/monitor_scripts/mysql_port_discovery.sh
# 判断配置文件是否存在
[ -f "${AGENT_CONF}" ] || { echo "File ${AGENT_CONF} does not exist.";exit 1;}
include=`grep ‘^Include‘ ${AGENT_CONF} | cut -d‘=‘ -f2`
# 在配置文件中添加自定义参数
if [ -d "$include" ];then
cat > $include/mysql_lld.conf << ‘EOF‘
UserParameter=mysql_port_discovery[*],/bin/bash /etc/zabbix/monitor_scripts/mysql_port_discovery.sh $1
UserParameter=mysql_status[*],mysql -h 127.0.0.1 -P $1 -uzabbix -pzabbix -N -e "show global status where Variable_name=‘$2‘" | cut -f2
UserParameter=mysql_ping[*],mysqladmin -h 127.0.0.1 -P $1 -uzabbix -pzabbix ping | grep -c alive
EOF
else
grep -q ‘^UserParameter=mysql_port_discovery‘ ${AGENT_CONF} || cat >> ${AGENT_CONF} << ‘EOF‘
UserParameter=mysql_port_discovery[*],/bin/bash /etc/zabbix/monitor_scripts/mysql_port_discovery.sh $1
UserParameter=mysql_status[*],mysql -h 127.0.0.1 -P $1 -uzabbix -pzabbix -N -e "show global status where Variable_name=‘$2‘" | cut -f2
UserParameter=mysql_ping[*],mysqladmin -h 127.0.0.1 -P $1 -uzabbix -pzabbix ping | grep -c alive
EOF
fi
# 手动MySQL授权,添加zabbix账户
echo "请在所有MySQL实例中添加zabbix账户,执行> GRANT PROCESS ON *.* TO ‘zabbix‘@‘127.0.0.1‘ identified BY ‘zabbix‘;flush privileges;"
# 重启agent服务
[ -f ‘/etc/init.d/zabbix-agent‘ ] && /etc/init.d/zabbix-agent restart || echo "需手动重启zabbix agent服务."
# 授权zabbix用户无密码运行netstat命令
chmod +w /etc/sudoers
sed -i ‘s/^\(Defaults\s\+requiretty\)/#\1/‘ /etc/sudoers
grep -q ‘^zabbix ALL=(ALL).*netstat‘ /etc/sudoers || echo ‘zabbix ALL=(ALL) NOPASSWD: /bin/netstat‘ >> /etc/sudoers
chmod 440 /etc/sudoers
# 关闭SELinux
setenforce 0
sed -i ‘/^SELINUX=/c\SELINUX=disabled‘ /etc/sysconfig/selinux
sed -i ‘/^SELINUX=/c\SELINUX=disabled‘ /etc/selinux/config脚本执行完毕后,还需要手动MySQL授权,在所有实例中添加zabbix账户:
mysql> GRANT PROCESS ON *.* TO ‘zabbix‘@‘127.0.0.1‘ identified BY ‘zabbix‘; mysql> flush privileges;
在zabbix server端执行zabbix_get命令测试:
shell# zabbix_get -s 115.238.xxx.xxx -k ‘mysql_port_discovery[mysql]‘
{
"data":[
{"{#MYSQLPORT}":"3306"}
]
}
shell# zabbix_get -s 115.238.xxx.xxx -k ‘mysql_status[3306,Uptime]‘
1295092
shell# zabbix_get -s 115.238.xxx.xxx -k ‘mysql_ping[3306]‘
1 都能返回数据,说明客户端的MySQL监控部署好了。
二、WEB端
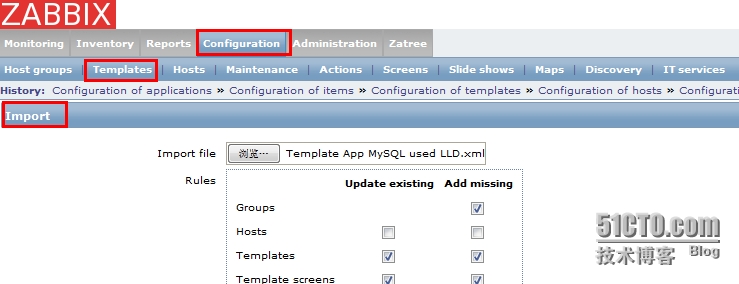
1、导入模板
下载附件模板文件(Template App MySQL used LLD.xml)后,导入到zabbix里。
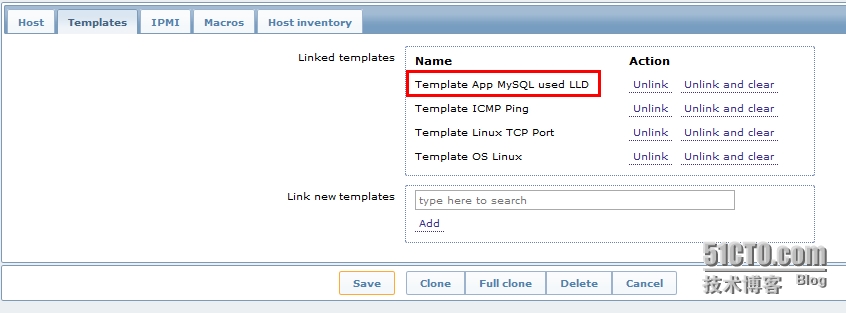
2、创建主机并链接模板
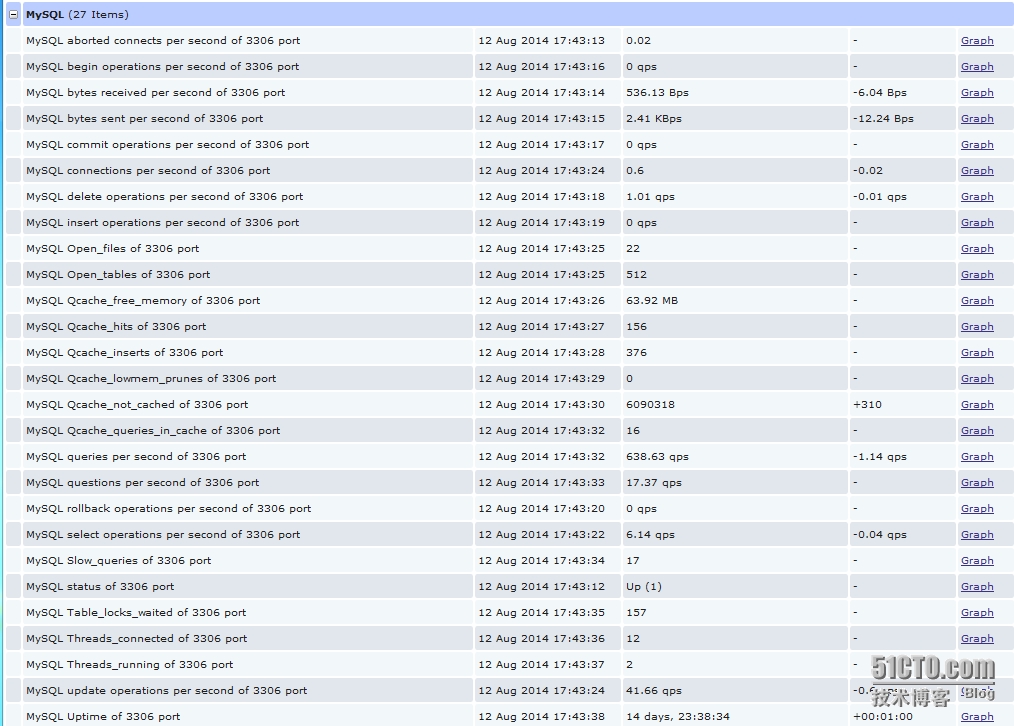
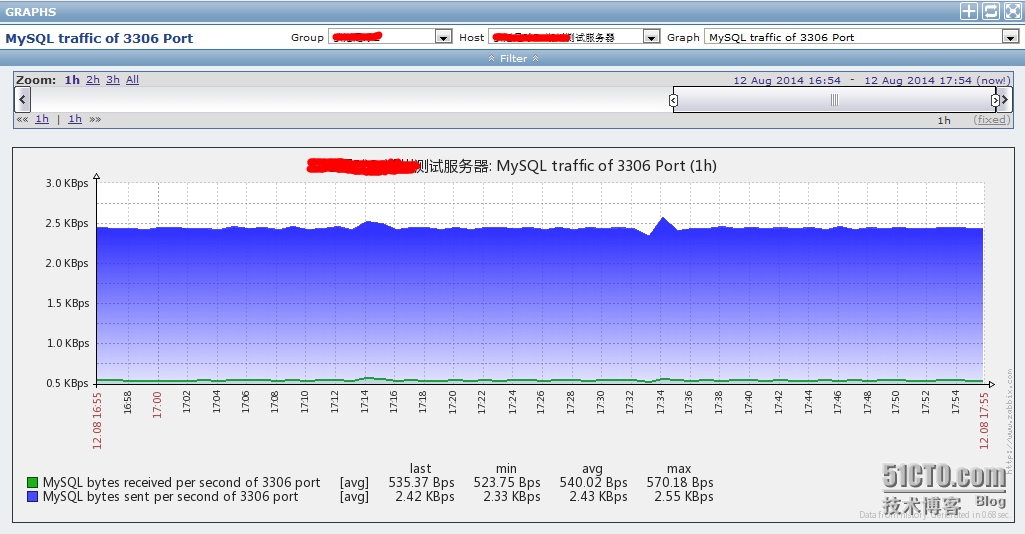
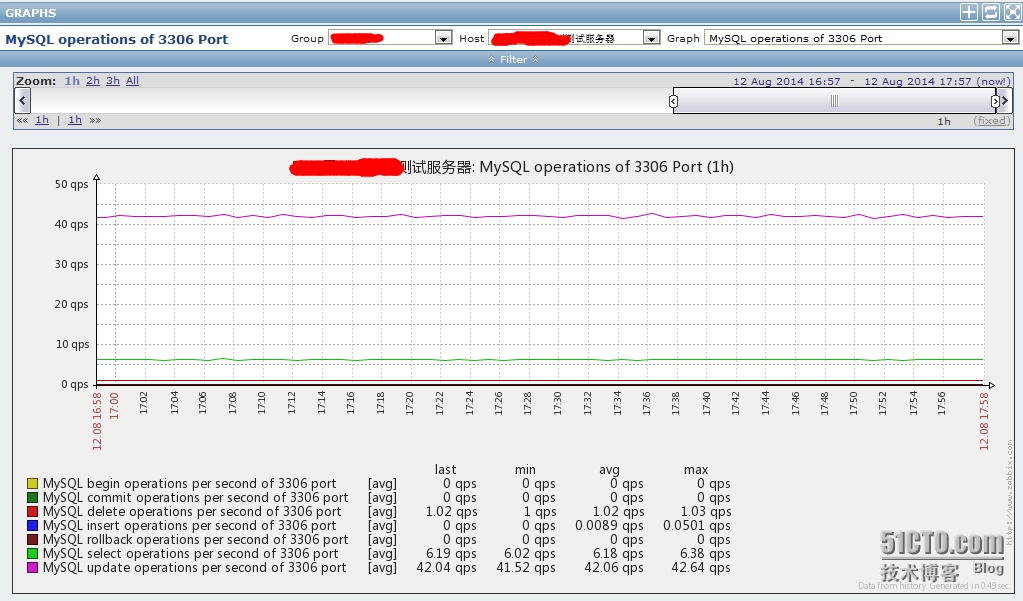
3、数据展示
本文出自 “启程-Linux技术博客” 博客,请务必保留此出处http://qicheng0211.blog.51cto.com/3958621/1539101
郑重声明:本站内容如果来自互联网及其他传播媒体,其版权均属原媒体及文章作者所有。转载目的在于传递更多信息及用于网络分享,并不代表本站赞同其观点和对其真实性负责,也不构成任何其他建议。