vpn案例2:vpn server和网关不在同一台上面
这里主要写的是vpn server和网关不在同一台服务器上的场景配置
一、环境
网关 eth0:192.168.3.80 gateway
网关 eth1:172.16.1.254 gateway
内网服务器 eth0:172.16.1.2 client
vpn服务器 eth0:172.16.1.1 vpn-server
外网客户端 IP:192.168.3.2 win7
二、安装yum源,同步时间
这我们的环境只能直接连上gateway,我们所有的操作都通过gateway做跳板连接到vpn-server上进行
因为这里的安装需要联网才能进行,我们临时将vpnserver的IP地址改为192.168.3.77,安装完成后改回172.16.1.1
[root@vpn-server ~]# hostname vpn-server [root@vpn-server ~]# rpm -ivh http://dl.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm Retrieving http://dl.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm warning: /var/tmp/rpm-tmp.wmr2p0: Header V3 RSA/SHA256 Signature, key ID 0608b895: NOKEY Preparing... ########################################### [100%] 1:epel-release ########################################### [100%] [root@vpn-server ~]# sed -i ‘s@#b@b@g‘ /etc/yum.repos.d/epel.repo [root@vpn-server ~]# sed -i ‘s@mirrorlist@#mirrorlist@g‘ /etc/yum.repos.d/epel.repo [root@vpn-server ~]# yum install ntpdate -y [root@vpn-server ~]# echo "*/10 * * * * /usr/sbin/ntpdate asia.pool.ntp.org &>/dev/null" >/var/spool/cron/root [root@vpn-server ~]# crontab -l */10 * * * * /usr/sbin/ntpdate asia.pool.ntp.org &>/dev/null
三、安装基础软件
[root@vpn-server ~]# yum install openssl openssl-devel lzo -y
四、安装openvpn和easy-rsa
[root@vpn-server ~]# yum install openvpn easy-rsa -y
到这里联网的部分已操作完,现在讲IP改回到172.16.1.1,之后的所有操作都通过gateway做跳板机来进行
#检查与vpn-server的连通性 [root@gateway ~]# ping 172.16.1.1 PING 172.16.1.1 (172.16.1.1) 56(84) bytes of data. 64 bytes from 172.16.1.1: icmp_seq=1 ttl=64 time=6.51 ms ^C --- 172.16.1.1 ping statistics --- 1 packets transmitted, 1 received, 0% packet loss, time 895ms rtt min/avg/max/mdev = 6.518/6.518/6.518/0.000 ms #通过ssh连接到vpn-server上进行操作 [root@gateway ~]# ssh 172.16.1.1 [email protected]‘s password: Last login: Thu May 28 14:39:31 2015 from 192.168.3.2 [root@vpn-server ~]# hostname vpn-server #修改vars文件信息 [root@vpn-server ~]# cd /usr/share/easy-rsa/2.0/ [root@vpn-server 2.0]# vim vars export KEY_COUNTRY="CN" export KEY_PROVINCE="GUANGDONG" export KEY_CITY="GUANGZHOU" export KEY_ORG="MY COMPANY" export KEY_EMAIL="[email protected]" #重新加载环境变量 [root@vpn-server 2.0]# source vars NOTE: If you run ./clean-all, I will be doing a rm -rf on /usr/share/easy-rsa/2.0/keys #清除所有证书和相关文件 [root@vpn-server 2.0]# ./clean-all #生成新的根证书和根秘钥 [root@vpn-server 2.0]# ./build-ca #整个过程直接回车 Generating a 2048 bit RSA private key .............................+++ .+++ writing new private key to ‘ca.key‘ ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. ----- Country Name (2 letter code) [CN]: State or Province Name (full name) [GUANGDONG]: Locality Name (eg, city) [GUANGZHOU]: Organization Name (eg, company) [MY COMPANY]: Organizational Unit Name (eg, section) [MyOrganizationalUnit]: Common Name (eg, your name or your server‘s hostname) [MY COMPANY CA]: Name [EasyRSA]: Email Address [[email protected]]:
给服务器端生成证书和秘钥
[root@vpn-server 2.0]# ./build-key-server server #提示(y/n),输入y Generating a 2048 bit RSA private key ............+++ ..................................................................................................+++ writing new private key to ‘server.key‘ ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. ----- Country Name (2 letter code) [CN]: State or Province Name (full name) [GUANGDONG]: Locality Name (eg, city) [GUANGZHOU]: Organization Name (eg, company) [MY COMPANY]: Organizational Unit Name (eg, section) [MyOrganizationalUnit]: Common Name (eg, your name or your server‘s hostname) [server]: Name [EasyRSA]: Email Address [[email protected]]: Please enter the following ‘extra‘ attributes to be sent with your certificate request A challenge password []: An optional company name []: Using configuration from /usr/share/easy-rsa/2.0/openssl-1.0.0.cnf Check that the request matches the signature Signature ok The Subject‘s Distinguished Name is as follows countryName :PRINTABLE:‘CN‘ stateOrProvinceName :PRINTABLE:‘GUANGDONG‘ localityName :PRINTABLE:‘GUANGZHOU‘ organizationName :PRINTABLE:‘MY COMPANY‘ organizationalUnitName:PRINTABLE:‘MyOrganizationalUnit‘ commonName :PRINTABLE:‘server‘ name :PRINTABLE:‘EasyRSA‘ emailAddress :IA5STRING:‘[email protected]‘ Certificate is to be certified until May 25 06:54:46 2025 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
给vpn客户端创建证书和秘钥,这里我们给win7-2创建
[root@vpn-server 2.0]# ./build-key win7-2 Generating a 2048 bit RSA private key ........................+++ .........................................................................................+++ writing new private key to ‘win7-2.key‘ ----- You are about to be asked to enter information that will be incorporated into your certificate request. What you are about to enter is what is called a Distinguished Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, If you enter ‘.‘, the field will be left blank. ----- Country Name (2 letter code) [CN]: State or Province Name (full name) [GUANGDONG]: Locality Name (eg, city) [GUANGZHOU]: Organization Name (eg, company) [MY COMPANY]: Organizational Unit Name (eg, section) [MyOrganizationalUnit]: Common Name (eg, your name or your server‘s hostname) [win7-2]: Name [EasyRSA]: Email Address [[email protected]]: Please enter the following ‘extra‘ attributes to be sent with your certificate request A challenge password []: An optional company name []: Using configuration from /usr/share/easy-rsa/2.0/openssl-1.0.0.cnf Check that the request matches the signature Signature ok The Subject‘s Distinguished Name is as follows countryName :PRINTABLE:‘CN‘ stateOrProvinceName :PRINTABLE:‘GUANGDONG‘ localityName :PRINTABLE:‘GUANGZHOU‘ organizationName :PRINTABLE:‘MY COMPANY‘ organizationalUnitName:PRINTABLE:‘MyOrganizationalUnit‘ commonName :PRINTABLE:‘win7-2‘ name :PRINTABLE:‘EasyRSA‘ emailAddress :IA5STRING:‘[email protected]‘ Certificate is to be certified until May 25 06:56:11 2025 GMT (3650 days) Sign the certificate? [y/n]:y 1 out of 1 certificate requests certified, commit? [y/n]y Write out database with 1 new entries Data Base Updated
生成Diffie Hellman文件
#生成过程可能有点慢,等待一会就好 [root@vpn-server 2.0]# ./build-dh #生成ta.key文件(防DDos攻击、UDP淹没等恶意攻击) [root@vpn-server 2.0]# openvpn --genkey --secret keys/ta.key
操作完成后查看keys路径下的文件
[root@vpn-server 2.0]# pwd /usr/share/easy-rsa/2.0 [root@vpn-server 2.0]# ll keys/ total 88 -rw-r--r-- 1 root root 5604 May 28 14:54 01.pem -rw-r--r-- 1 root root 5483 May 28 14:56 02.pem -rw-r--r-- 1 root root 1801 May 28 14:53 ca.crt -rw------- 1 root root 1708 May 28 14:53 ca.key -rw-r--r-- 1 root root 424 May 28 14:59 dh2048.pem -rw-r--r-- 1 root root 294 May 28 14:56 index.txt -rw-r--r-- 1 root root 21 May 28 14:56 index.txt.attr -rw-r--r-- 1 root root 21 May 28 14:54 index.txt.attr.old -rw-r--r-- 1 root root 147 May 28 14:54 index.txt.old -rw-r--r-- 1 root root 3 May 28 14:56 serial -rw-r--r-- 1 root root 3 May 28 14:54 serial.old -rw-r--r-- 1 root root 5604 May 28 14:54 server.crt -rw-r--r-- 1 root root 1098 May 28 14:54 server.csr -rw------- 1 root root 1704 May 28 14:54 server.key -rw------- 1 root root 636 May 28 15:01 ta.key -rw-r--r-- 1 root root 5483 May 28 14:56 win7-2.crt -rw-r--r-- 1 root root 1098 May 28 14:56 win7-2.csr -rw------- 1 root root 1704 May 28 14:56 win7-2.key
五、创建服务端配置文件
# 在openvpn的配置目录下新建一个keys目录
[root@vpn-server 2.0]# mkdir -p /etc/openvpn/keys
#将openvpn服务端需要用到的证书和秘钥复制到/etc/openvpn/keys目录下
[root@vpn-server 2.0]# cp /usr/share/easy-rsa/2.0/keys/{ca.crt,server.{crt,key},dh2048.pem,ta.key} /etc/openvpn/keys/
[root@vpn-server 2.0]# ll /etc/openvpn/keys/
total 24
-rw-r--r-- 1 root root 1801 May 28 15:04 ca.crt
-rw-r--r-- 1 root root 424 May 28 15:04 dh2048.pem
-rw-r--r-- 1 root root 5604 May 28 15:04 server.crt
-rw------- 1 root root 1704 May 28 15:04 server.key
-rw------- 1 root root 636 May 28 15:04 ta.key
#复制服务端配置文件到/etc/openvpn
[root@vpn-server 2.0]# cp /usr/share/doc/openvpn-2.3.6/sample/sample-config-files/server.conf /etc/openvpn/
#编辑server.conf文件参数
[root@vpn-server ~]# egrep -v "^#|^$|^;" /etc/openvpn/server.conf
#openvpn监听的端口
port 1194
#这里请使用tcp协议,不要使用udp
proto tcp
dev tun
#证书和秘钥的路径,我们放在/etc/openvpn/keys目录下
ca keys/ca.crt
cert keys/server.crt
key keys/server.key # This file should be kept secret
dh keys/dh2048.pem
#这里是默认的虚拟局域网网段,不要和实际网段相同
server 10.8.0.0 255.255.255.0
ifconfig-pool-persist ipp.txt
#这里因为我的内网是172.16.1.0/24网段的,所以我修改成172.16.1.0网段
push "route 172.16.1.0 255.255.255.0"
client-to-client
keepalive 10 120
comp-lzo
persist-key
persist-tun
#这是openvpn的日志文件,默认在/etc/openvpn/openvpn.log
status openvpn-status.log
#启用日志追加
log-append openvpn.log
#调试级别
verb 4启动openvpn服务
#将openvpn添加到开机自启动 [root@vpn-server 2.0]# chkconfig openvpn on [root@vpn-server 2.0]# service openvpn start Starting openvpn: [ OK ] [root@vpn-server 2.0]# netstat -anpt |grep vpn tcp 0 0 0.0.0.0:1194 0.0.0.0:* LISTEN 2339/openvpn [root@vpn-server 2.0]# iptables -I INPUT -p tcp --dport 1194 -j ACCEPT [root@vpn-server 2.0]# iptables -L -n Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:1194 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) target prot opt source destination REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain OUTPUT (policy ACCEPT) target prot opt source destination
六、客户端安装及配置
OpenVPN 2.3.3 Windows 32位 安装文件:
http://swupdate.openvpn.org/community/releases/openvpn-install-2.3.3-I002-i686.exe
OpenVPN 2.3.3 Windows 64位 安装文件:
http://swupdate.openvpn.org/community/releases/openvpn-install-2.3.3-I002-x86_64.exe
将openvpn服务器上的ca.crt,win7-2.crt,win7-2.csr,win7-2.key,下载到C:\Program Files\OpenVPN\config目录下
新建客户端配置文件openvpn.ovpn,因为这里的vpn-server没有和网关在一起,我们要将vpn-server的地址指向192.168.3.80
openvpn.ovpn 文件内容:
client dev tun # 改为tcp proto tcp remote 192.168.3.80 1194 # OpenVPN服务器的外网IP和端口 resolv-retry infinite nobind persist-key persist-tun ca ca.crt cert win7.crt # win7的证书 key win7.key # win7的密钥 ns-cert-type server # 去掉前面的注释 #tls-auth ta.key 1 comp-lzo verb 3
开始连接vpn-server,此时应该是连接不上的,应该在gateway上配置DNAT规则和开启路由转发功能
[root@gateway ~]# iptables -t nat -A PREROUTING -p tcp --dport 1194 -j DNAT --to 172.16.1.1:1194 #编辑文件/etc/sysctl.conf打开路由转发功能 [root@gateway ~]# vim /etc/sysctl.conf [root@gateway ~]# sysctl -p net.ipv4.ip_forward = 1 #确保这项是1 net.ipv4.conf.default.rp_filter = 1 net.ipv4.conf.default.accept_source_route = 0 kernel.sysrq = 0 kernel.core_uses_pid = 1 net.ipv4.tcp_syncookies = 1 kernel.msgmnb = 65536 kernel.msgmax = 65536 kernel.shmmax = 68719476736 kernel.shmall = 4294967296 #因为iptables的filter表的FORWARD默认reject掉了路由转发,我们需要打开该功能 [root@gateway ~]# iptables -t filter -F FORWARD [root@gateway ~]# iptables -t filter -L -n Chain INPUT (policy ACCEPT) target prot opt source destination ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 state RELATED,ESTABLISHED ACCEPT icmp -- 0.0.0.0/0 0.0.0.0/0 ACCEPT all -- 0.0.0.0/0 0.0.0.0/0 ACCEPT tcp -- 0.0.0.0/0 0.0.0.0/0 state NEW tcp dpt:22 REJECT all -- 0.0.0.0/0 0.0.0.0/0 reject-with icmp-host-prohibited Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination [root@gateway ~]# iptables -t nat -L -n Chain PREROUTING (policy ACCEPT) target prot opt source destination DNAT tcp -- 0.0.0.0/0 0.0.0.0/0 tcp dpt:1194 to:172.16.1.1:1194 Chain POSTROUTING (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
到此我们再连接vpn-server
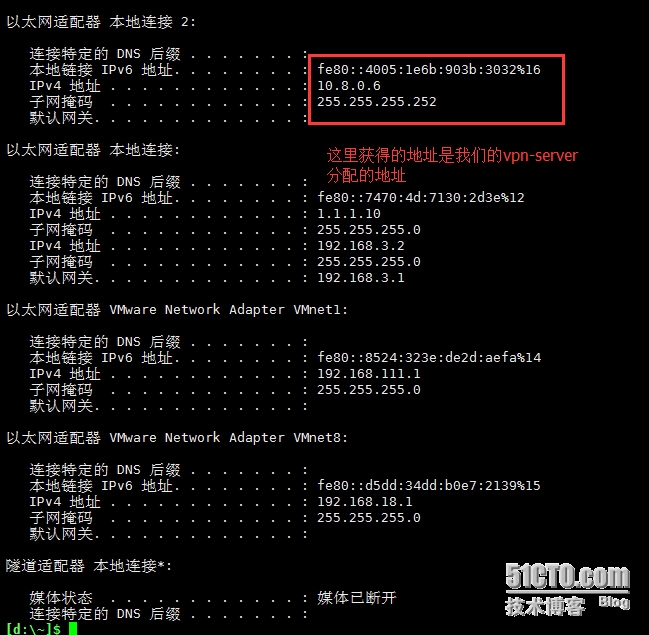
检查vpn-server的连通性
[d:\~]$ ping 172.16.1.1 正在 Ping 172.16.1.1 具有 32 字节的数据: 来自 172.16.1.1 的回复: 字节=32 时间=2ms TTL=64 来自 172.16.1.1 的回复: 字节=32 时间=1ms TTL=64 来自 172.16.1.1 的回复: 字节=32 时间=1ms TTL=64 172.16.1.1 的 Ping 统计信息: 数据包: 已发送 = 3,已接收 = 3,丢失 = 0 (0% 丢失), 往返行程的估计时间(以毫秒为单位): 最短 = 1ms,最长 = 2ms,平均 = 1ms [d:\~]$ ping 172.16.1.2 正在 Ping 172.16.1.2 具有 32 字节的数据: 请求超时。 172.16.1.2 的 Ping 统计信息: 数据包: 已发送 = 1,已接收 = 0,丢失 = 1 (100% 丢失), #从上面能看出我们只能ping通vpn-server,内网的其余服务器是ping不通的,我们需要在vpn-server开启路由转发功能和SNAT规则 [root@vpn-server ~]# iptables -t filter -F FORWARD [root@vpn-server ~]# vim /etc/sysctl.conf [root@vpn-server ~]# sysctl -p net.ipv4.ip_forward = 1 #确保这一项是1 net.ipv4.conf.default.rp_filter = 1 net.ipv4.conf.default.accept_source_route = 0 kernel.sysrq = 0 kernel.core_uses_pid = 1 net.ipv4.tcp_syncookies = 1 kernel.msgmnb = 65536 kernel.msgmax = 65536 kernel.shmmax = 68719476736 kernel.shmall = 4294967296 #配置SNAT [root@vpn-server ~]# iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -j SNAT --to 172.16.1.1 [root@vpn-server ~]# iptables -t nat -L -n Chain PREROUTING (policy ACCEPT) target prot opt source destination Chain POSTROUTING (policy ACCEPT) target prot opt source destination SNAT all -- 10.8.0.0/24 0.0.0.0/0 to:172.16.1.1 Chain OUTPUT (policy ACCEPT) target prot opt source destination #配置完成后检查是否能ping 通内网服务器 [d:\~]$ ping 172.16.1.2 正在 Ping 172.16.1.2 具有 32 字节的数据: 来自 172.16.1.2 的回复: 字节=32 时间=4ms TTL=63 来自 172.16.1.2 的回复: 字节=32 时间=1ms TTL=63 来自 172.16.1.2 的回复: 字节=32 时间=1ms TTL=63 来自 172.16.1.2 的回复: 字节=32 时间=1ms TTL=63 172.16.1.2 的 Ping 统计信息: 数据包: 已发送 = 4,已接收 = 4,丢失 = 0 (0% 丢失), 往返行程的估计时间(以毫秒为单位): 最短 = 1ms,最长 = 4ms,平均 = 1ms [d:\~]$ ping 172.16.1.254 正在 Ping 172.16.1.254 具有 32 字节的数据: 来自 172.16.1.254 的回复: 字节=32 时间=2ms TTL=63 来自 172.16.1.254 的回复: 字节=32 时间=1ms TTL=63 来自 172.16.1.254 的回复: 字节=32 时间=1ms TTL=63 来自 172.16.1.254 的回复: 字节=32 时间=1ms TTL=63 172.16.1.254 的 Ping 统计信息: 数据包: 已发送 = 4,已接收 = 4,丢失 = 0 (0% 丢失), 往返行程的估计时间(以毫秒为单位): 最短 = 1ms,最长 = 2ms,平均 = 1ms #结果显示已能正常ping通内网服务器
此时办公点和内网都能互通了,要实现内部网络上网还需要在gateway上配置SANT规则
[root@gateway ~]# iptables -t nat -A POSTROUTING -s 172.16.1.0/24 -j SNAT --to 192.168.3.80 #内网服务器 [root@client ~]# route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 172.16.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0 169.254.0.0 0.0.0.0 255.255.0.0 U 1002 0 0 eth0 0.0.0.0 172.16.1.254 0.0.0.0 UG 0 0 0 eth0 [root@client ~]# ping baidu.com PING baidu.com (123.125.114.144) 56(84) bytes of data. 64 bytes from 123.125.114.144: icmp_seq=2 ttl=49 time=34.8 ms 64 bytes from 123.125.114.144: icmp_seq=3 ttl=50 time=35.1 ms 64 bytes from 123.125.114.144: icmp_seq=4 ttl=50 time=35.6 ms ^C --- baidu.com ping statistics --- 4 packets transmitted, 3 received, 25% packet loss, time 3182ms rtt min/avg/max/mdev = 34.810/35.191/35.604/0.390 ms #vpn-server [root@vpn-server ~]# route -n Kernel IP routing table Destination Gateway Genmask Flags Metric Ref Use Iface 10.8.0.2 0.0.0.0 255.255.255.255 UH 0 0 0 tun0 10.8.0.0 10.8.0.2 255.255.255.0 UG 0 0 0 tun0 172.16.1.0 0.0.0.0 255.255.255.0 U 0 0 0 eth0 169.254.0.0 0.0.0.0 255.255.0.0 U 1002 0 0 eth0 0.0.0.0 172.16.1.254 0.0.0.0 UG 0 0 0 eth0 [root@vpn-server ~]# hostname vpn-server [root@vpn-server ~]# ping baidu.com PING baidu.com (220.181.57.217) 56(84) bytes of data. 64 bytes from 220.181.57.217: icmp_seq=1 ttl=52 time=40.3 ms 64 bytes from 220.181.57.217: icmp_seq=2 ttl=52 time=38.7 ms ^C --- baidu.com ping statistics --- 2 packets transmitted, 2 received, 0% packet loss, time 1371ms rtt min/avg/max/mdev = 38.718/39.543/40.369/0.849 ms
本文出自 “ly36843运维” 博客,请务必保留此出处http://ly36843.blog.51cto.com/3120113/1655991
郑重声明:本站内容如果来自互联网及其他传播媒体,其版权均属原媒体及文章作者所有。转载目的在于传递更多信息及用于网络分享,并不代表本站赞同其观点和对其真实性负责,也不构成任何其他建议。