Linux下的DNS服务器配置实践(一)
【实验说明】
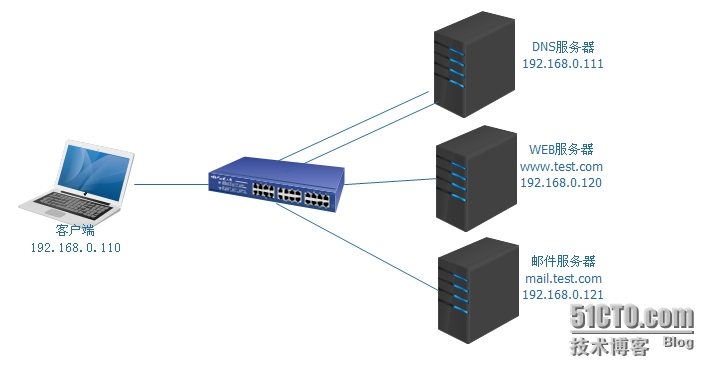
目的:在Linux上安装bind,配置正向解析与方向解析,实现基本的域名解析服务。
【配置过程】
1、安装bind;
[root@www ~]# yum install bind -y Loaded plugins: fastestmirror, refresh-packagekit, security -----略----- Complete!
2、修改主配置文件;
[root@www ~]#vim /etc/named.conf
// named.conf
//
// Provided by Red Hat bind package to configure the ISC BIND named(8) DNS
// server as a caching only nameserver (as a localhost DNS resolver only).
//
// See /usr/share/doc/bind*/sample/ for example named configuration files.
//
#“//”表示该行为注释信息,如果不想启用某选项在其行首加上//即可;
options {
// listen-on port 53 { 127.0.0.1; }; #指定在那个地址上的多少号端口监听;
// listen-on-v6 port 53 { ::1; }; #监听在所有主机上的53号端口上;
directory "/var/named"; #定义工作目录;
dump-file "/var/named/data/cache_dump.db";#指定缓存存储文件;
statistics-file "/var/named/data/named_stats.txt";#记录内存使用情况的统计信息;
memstatistics-file "/var/named/data/named_mem_stats.txt";
// allow-query { localhost; }; #定义允许查询的主机;
recursion yes;#是否允许递归;
// dnssec-enable yes;
// dnssec-validation yes;
// dnssec-lookaside auto;
/* Path to ISC DLV key */
// bindkeys-file "/etc/named.iscdlv.key";
// managed-keys-directory "/var/named/dynamic";
};
logging { #日志信息;
channel default_debug {
file "data/named.run";
severity dynamic;
};
};
zone "." IN { #根域的定义;
type hint;
file "named.ca";
};
include "/etc/named.rfc1912.zones";
//include "/etc/named.root.key";
#-----至此,如果不做其他修改,启动DNS服务,此服务器便是一台缓存DNS服务器!-------
[root@www ~]# vim /etc/named.rfc1912.zones #通过修改此配置文件,配置正向反向解析区域;
#---略---
zone "test.com" IN { #定义“test.com”的正向解析区域;
type master; #定义服务器的类型为主服务器;
file "test.com.zone" #指定正向解析区域文件;
};
zone "0.168.192.in-addr.arpa" IN { #定义“test.com”的反向解析区域;
type master;
file "192.168.0.arpa";
};
[root@www named]# named-checkconf /etc/named.conf #检验配置文件是否有语法错误;
[root@www named]#3、为每一个区域提供解析库;
[root@www named]# vim /var/named/test.com.zone #配置正向解析库; $TTL 86400 #默认ttl值; @ IN SOA ns.test.com. admin.test.com. ( 2015051105 ;#解析库的版本号,例如2015051106 ,这个序列号的作用是当辅域名服务 器来复制这个文件的时候,如果号码增加了就复制; 2H ;#周期性同步的时间间隔 10M ;#重试的时间间隔,当辅域名服务试图在主服务器上查询更新时,而连接失败了, 辅域名服务器每隔多久访问主域名服务器; 7D;#过期时长; 1D ) ;#否定答案的统一缓存时长; IN NS ns.test.com. #定义域名服务器; IN MX 10 mail.test.com. #邮件服务器; www IN A 192.168.0.120 mail IN A 192.168.0.121 ns IN A 192.168.0.111 pop3 IN CNAME mail.test.com.#邮件服务器的别名; [root@www named]# named-checkzone "test.com" ./test.com.zone #检查解析库是否有错误; zone test.com/IN: loaded serial 2015051105 OK [root@www named]# vim /var/named/192.168.0.arpa #配置反向解析库; $TTL 86400 @ IN SOA ns.test.com. admin.test.com. ( 2015051105 2H 10M 7D 1D ) IN NS ns.test.com. 120 IN PTR www.test.com. 121 IN PTR mail.test.com. 111 IN PTR ns.test.com. [root@www named]# named-checkzone "0.168.192.in-addr.arpa" ./192.168.0.arpa #检查解析库是否有错误; zone 0.168.192.in-addr.arpa/IN: loaded serial 2015051105 OK [root@www named]# service named start #启动DNS服务; Starting named: [ OK ] #——至此基本的DNS服务配置完成——————
【测试结果】
[root@www named]# host -t NS test.com 192.168.0.111 #通过0.111这个服务器解析test.com的域名主机; Using domain server: Name: 192.168.0.111 Address: 192.168.0.111#53 Aliases: test.com name server ns.test.com. #OK,域名主机就是ns.test.com.; [root@www named]# host -t MX test.com 192.168.0.111 Using domain server: Name: 192.168.0.111 Address: 192.168.0.111#53 Aliases: test.com mail is handled by 10 mail.test.com. #OK,邮件服务器就是mail.test.com.; [root@www named]# host -t A www.test.com 192.168.0.111 Using domain server: Name: 192.168.0.111 Address: 192.168.0.111#53 Aliases: www.test.com has address 192.168.0.120 #解析成功; [root@www named]# host -t A mail.test.com 192.168.0.111 Using domain server: Name: 192.168.0.111 Address: 192.168.0.111#53 Aliases: mail.test.com has address 192.168.0.121 [root@www named]# dig -t A www.test.com @192.168.0.111 ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> -t A www.test.com @192.168.0.111 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 13687 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1 ;; QUESTION SECTION: #查询的问题; ;www.test.com. IN A ;; ANSWER SECTION: #查询的结果; www.test.com. 86400 IN A 192.168.0.120 ;; AUTHORITY SECTION: #权威回答的来源; test.com. 86400 IN NS ns.test.com. ;; ADDITIONAL SECTION: #权威回答的来源的补充说明; ns.test.com. 86400 IN A 192.168.0.111 ;; Query time: 1 msec ;; SERVER: 192.168.0.111#53(192.168.0.111) ;; WHEN: Fri May 15 06:21:21 2015 ;; MSG SIZE rcvd: 79 [root@www named]# dig -x 192.168.0.120 @192.168.0.111 ; <<>> DiG 9.8.2rc1-RedHat-9.8.2-0.17.rc1.el6_4.6 <<>> -x 192.168.0.120 @192.168.0.111 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 27168 ;; flags: qr aa rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 1 ;; QUESTION SECTION: ;120.0.168.192.in-addr.arpa. IN PTR ;; ANSWER SECTION: 120.0.168.192.in-addr.arpa. 86400 IN PTR www.test.com. ;; AUTHORITY SECTION: 0.168.192.in-addr.arpa. 86400 IN NS ns.test.com. ;; ADDITIONAL SECTION: ns.test.com. 86400 IN A 192.168.0.111 ;; Query time: 8 msec ;; SERVER: 192.168.0.111#53(192.168.0.111) ;; WHEN: Fri May 15 06:22:25 2015 ;; MSG SIZE rcvd: 103
客户端测试工具:
1、host -t RRType NAME [SERVER]
例如:host -t NS test.com 192.168.0.111
host -t A www.test.com 192.168.0.111
注意:-t指定资源类型时,其后的名称必须是资源记录允许使用的名称;当不指定SERVER时默认使用的是/etc/resolv.conf里面设置的DNS。
2、nslookup
nslookup>
server IP: 指定DNS服务器地址;
set type={A|SOA|NS|MX}
name
3、dig
dig -t TYPE name @server
类型可使用:AXFR 完全区域传送,显示所有的资源记录;
例如: dig -t AXFR test.com @192.168.0.111
测试反解不使用-t PTR,而使用-x选项 例:diag -x 192.168.0.120 @192.168.0.111
dig: 查询选项
+trace 启动路由跟踪;
+notrace
+recurse 启用递归;
+norecurse
本文出自 “飞奔的蜗牛” 博客,请务必保留此出处http://ljmsky.blog.51cto.com/2878/1651416
郑重声明:本站内容如果来自互联网及其他传播媒体,其版权均属原媒体及文章作者所有。转载目的在于传递更多信息及用于网络分享,并不代表本站赞同其观点和对其真实性负责,也不构成任何其他建议。