VPN案例之二思科防火墙与router通信
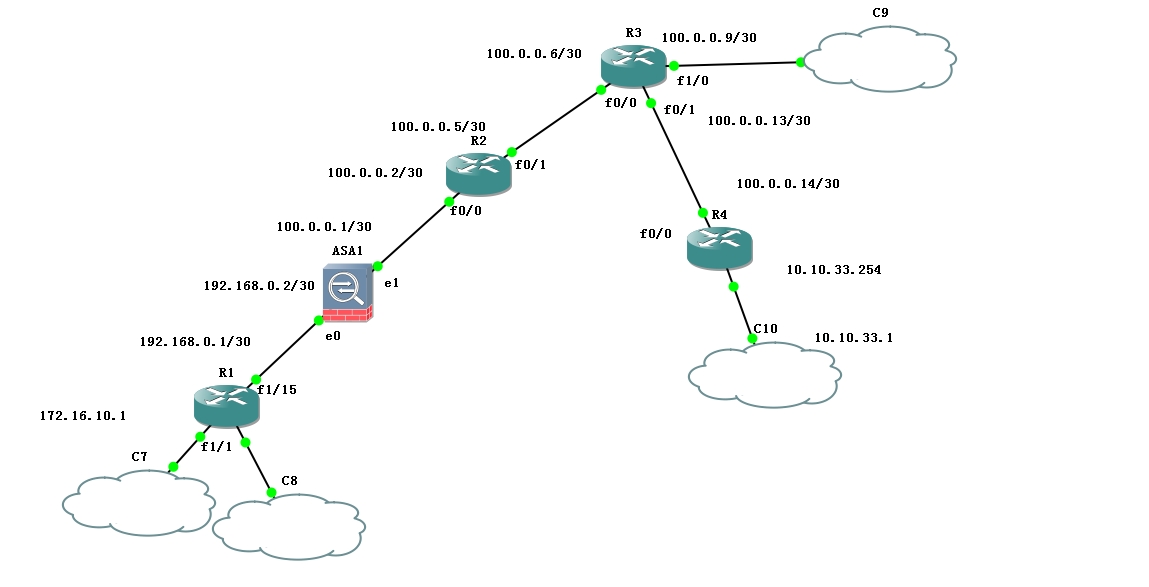
实验拓扑图:
项目场景:公司总部是广州,内网里面有两个VLAN,分别是”kaifabu”-172.16.10.0/24和”yewubu”-172.16.20.0/24,c9上搭建了一个iis web服务器用来模拟公网,R4路由接入上海的分公司,内网网段10.10.33.0/24。
1.广州总公司的172.16.20.0、24需要做PAT地址转换访问外网。
2.要求广州vlan 20 “shiwubu” 可以访问c9的web,vlan10 “kaifabu” 禁止访问c9的web, 上海分公司可以访问c9web。
3.需要在广州的ASA防火墙和上海分公司的R4路由之间做vpn,实现广州的vlan10和上海的内网实现通信
实验代码:
R1(neiwang):
en
vlan database
vlan 10 name kaifa
vlan 20 name qita
exit
conf t
int vlan 10
ip add 172.16.10.254 255.255.255.0
no sh
int vlan 20
ip add 172.16.20.254 255.255.255.0
no sh
exit
int f1/1
sw access vlan 10
no sh
int f1/2
sw access vlan 20
no sh
exit
int f1/15
no sw
ip add 192.168.0.1 255.255.255.252
no sh
exit
ip route 0.0.0.0 0.0.0.0 192.168.0.2
ASA1:
conf t
hostname ASA
domain-name dragon
int e0/0
nameif inside
ip add 192.168.0.2 255.255.255.252
no sh
int e0/1
nameif outside
ip add 100.0.0.1 255.255.255.252
no sh
exit
nat (inside) 2 172.16.20.0 255.255.255.0
global (outside) 2 inter
route outside 0 0 100.0.0.2
route inside 172.16.10.0 255.255.255.0 192.168.0.1
route inside 172.16.20.0 255.255.255.0 192.168.0.1
nat-control
access-list nonat extended permit ip 172.16.10.0 255.255.255.0 10.10.33.0 255.255.255.0
nat (inside) 0 access-list nonat
crypto isakmp enable outside
crypto isakmp policy 1
encryption aes
hash sha
authentication pre-share
group 1
exit
tunnel-group 100.0.0.14 type ipsec-l2l
tunnel-group 100.0.0.14 ipsec-attributes
pre-shared-key dragon-key
exit
access-list vpn1 extended permit ip 172.16.10.0 255.255.255.0 10.10.33.0 255.255.255.0
crypto ipsec transform-set dragon-set esp-aes esp-sha-hmac
crypto map dragon-map 1 match address vpn1
crypto map dragon-map 1 set peer 100.0.0.14
crypto map dragon-map 1 set transform-set dragon-set
crypto map dragon-map int outside
R2:
conf t
hostname router2
int f0/0
ip add 100.0.0.2 255.255.255.252
no sh
int f0/1
ip add 100.0.0.5 255.255.255.252
no sh
exit
ip route 172.16.10.0 255.255.255.0 100.0.0.1
ip route 0.0.0.0 0.0.0.0 100.0.0.6
R3(公网):
conf t
hostname ISP
int f0/0
ip add 100.0.0.6 255.255.255.252
no sh
int f1/0
no sw
ip add 100.0.0.9 255.255.255.252
no sh
int f0/1
ip add 100.0.0.13 255.255.255.252
no sh
exit
ip route 100.0.0.0 255.255.255.252 100.0.0.5
R4:
conf t
hostname SH
int f0/0
ip add 100.0.0.14 255.255.255.252
no sh
int f0/1
ip add 10.10.33.254 255.255.255.0
no sh
exit
ip route 0.0.0.0 0.0.0.0 100.0.0.13
access-list 100 deny ip 10.10.33.0 0.0.0.255 172.16.10.0 0.0.0.255
access-list 100 permit ip any any
ip nat inside source list 100 int f0/0 overload
int f0/0
ip nat outside
int f0/1
ip nat inside
exit
crypto isakmp policy 1
encryption aes
hash sha
authentication pre-share
group 1
crypto isakmp key 0 dragon-key address 100.0.0.1
access-list 101 permit ip 10.10.33.0 0.0.0.255 172.16.10.0 0.0.0.255
crypto ipsec transform-set dragon-set esp-aes esp-sha-hmac
mode tunnel
exit
crypto map dragon-map 1 ipsec-isakmp
set peer 100.0.0.1
set transform-set dragon-set
match address 101
interface f0/0
crypto map dragon-map
End
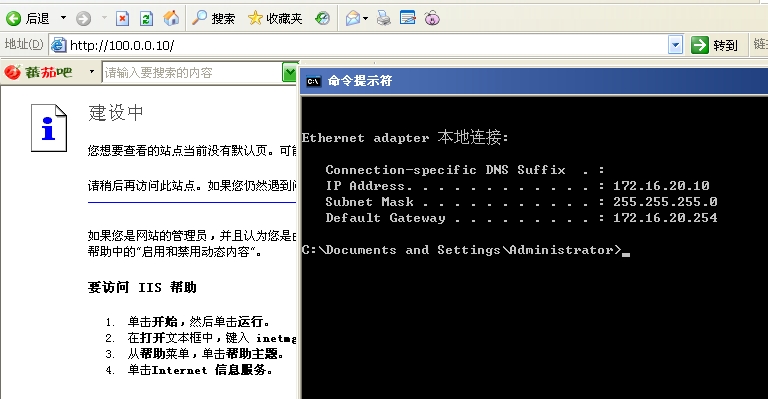
内网的172,.16.20.0网段可以访问(100.0.0.10)web
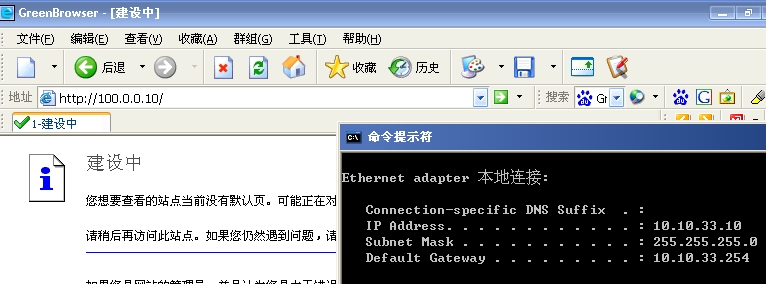
分公司10.10.33.0网段可以访问(100.0.0.10)web
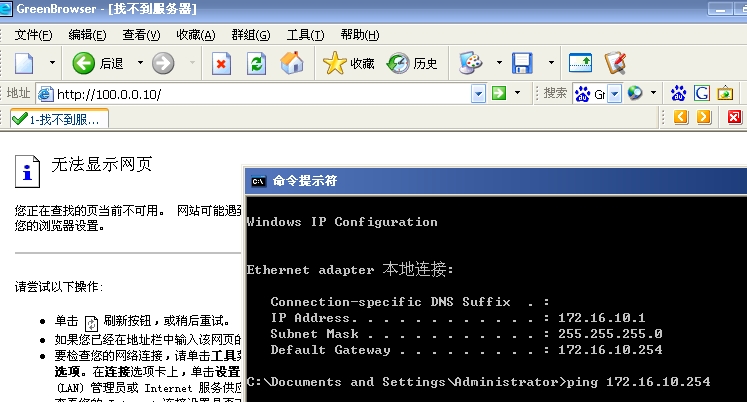
内网的172,.16.10.0网段可以访问(100.0.0.10)web
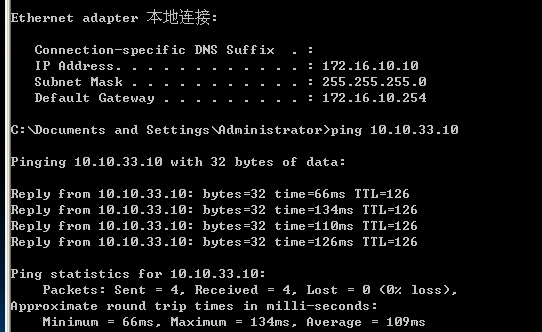
VPN正常通信:
本文出自 “龙爱雪琪” 博客,请务必保留此出处http://dragon123.blog.51cto.com/9152073/1568874
郑重声明:本站内容如果来自互联网及其他传播媒体,其版权均属原媒体及文章作者所有。转载目的在于传递更多信息及用于网络分享,并不代表本站赞同其观点和对其真实性负责,也不构成任何其他建议。