在Cisco ASA上实验 使用RRI的全互连Site to Site IPSec VPN
拓扑图如上。
说明:ASA1、2、3模拟分支边界网关,并启用PAT。R1、2、3模拟各内网设备。
要求:在ASA1、2、3上配置Site to Site VPN,实现全互联并配置反向路由注入(RRI),R1、2、3可以使用私有IP加密通信,不要求使用loopback IP通信;R1、2、3上有去往各私网的路由(通过RRI)。
配置如下:
ASA1:
ciscoasa>en ciscoasa# conf t //基本配置部分 ciscoasa(config)# hostname ASA1 ASA1(config)# int e0/0 ASA1(config-if)# nameif outside ASA1(config-if)# security-level 0 ASA1(config-if)# ip add 209.165.200.225 255.255.255.224 ASA1(config-if)# no shut ASA1(config-if)# int e0/1 ASA1(config-if)# nameif inside ASA1(config-if)# security-level 100 ASA1(config-if)# ip add 192.168.1.1 255.255.255.0 ASA1(config-if)# no shut ASA1(config-if)# exit ASA1(config)# nat (inside) 1 0 0 ASA1(config)# global (outside) 1 interface ASA1(config)# route outside 0 0 209.165.200.227 ASA1(config)# policy-map global_policy ASA1(config-pmap)# class inspection_default ASA1(config-pmap-c)# inspect icmp //默认ASA不监控ICMP流量,在此外加上可以使内网ping通外网 ASA1(config-pmap-c)# end ASA1#conf t //1、启用ISAKMP ASA1(config)# crypto isakmp enable outside //2、创建ISAKMP策略 ASA1(config)# crypto isakmp policy 1 ASA1(config-isakmp-policy)# encryption aes-256 ASA1(config-isakmp-policy)# hash sha ASA1(config-isakmp-policy)# group 5 ASA1(config-isakmp-policy)# lifetime 86400 ASA1(config-isakmp-policy)# authentication pre-share ASA1(config-isakmp-policy)# exit //3、创建隧道组 ASA1(config)# tunnel-group 209.165.201.1 type ipsec-l2l ASA1(config)# tunnel-group 209.165.201.1 ipsec-attributes ASA1(config-tunnel-ipsec)# pre-shared-key cisco123 ASA1(config-tunnel-ipsec)# exit ASA1(config)# tunnel-group 209.165.202.129 type ipsec-l2l ASA1(config)# tunnel-group 209.165.202.129 ipsec-attributes ASA1(config-tunnel-ipsec)# pre-shared-key cisco123 ASA1(config-tunnel-ipsec)# exit //4、定义IPSec策略 ASA1(config)# crypto ipsec transform-set AES-SHA esp-aes-256 esp-sha-hmac //5、创建加密映射集 ASA1(config)# access-list outside_cryptomap_1 remark To Encrypt Traffic from 192.168.1.0/24 to 10.10.1.0/24 ASA1(config)# access-list outside_cryptomap_1 extended permit ip 192.168.1.0 255.255.255.0 10.10.1.0 255.255.255.0 ASA1(config)# access-list outside_cryptomap_2 remark To Ecrypto Traffic from 192.168.1.0/24 to 172.16.1.0/24 ASA1(config)# access-list outside_cryptomap_2 extended permit ip 192.168.1.0 255.255.255.0 172.16.1.0 255.255.255.0 ASA1(config)# crypto map outside_map 1 match address outside_cryptomap_1 ASA1(config)# crypto map outside_map 1 set transform-set AES-SHA ASA1(config)# crypto map outside_map 1 set peer 209.165.201.1 ASA1(config)# crypto map outside_map 1 set reverse-route //配置RRI(反向路由注入) ASA1(config)# crypto map outside_map 2 match address outside_cryptomap_2 ASA1(config)# crypto map outside_map 2 set transform-set AES-SHA ASA1(config)# crypto map outside_map 2 set peer 209.165.202.129 ASA1(config)# crypto map outside_map 2 set reverse-route //配置RRI(反向路由注入) ASA1(config)# crypto map outside_map interface outside //6、启用OSPF动态路由并向内网路由器重新发布路由 ASA1(config)# router ospf 100 ASA1(config-router)# area 0 ASA1(config-router)# network 192.168.0.0 255.255.0.0 area 0 ASA1(config-router)# redistribute static subnets //将子网静态路由重发布到OSPF网络 ASA1(config-router)# exit //7、绕过NAT,为穿越VPN隧道的流量建立NAT豁免规则 ASA1(config)# access-list inside_nat0_outbound remark To Bypass NAT from 192.168.1.0/24 to 10.10.1.0/24 ASA1(config)# access-list inside_nat0_outbound extended permit ip 192.168.1.0 255.255.255.0 10.10.1.0 255.255.255.0 ASA1(config)# access-list inside_nat0_outbound remark To Bypass NAT from 192.168.1.0/24 to 172.16.1.0/24 ASA1(config)# access-list inside_nat0_outbound extended permit ip 192.168.1.0 255.255.255.0 172.16.1.0 255.255.255.0 ASA1(config)# nat (inside) 0 access-list inside_nat0_outbound ASA1(config)# wr
ASA2:
ciscoasa>en ciscoasa# conf t //基本配置部分 ciscoasa(config)# hostname ASA2 ASA2(config)# int e0/0 ASA2(config-if)# nameif outside ASA2(config-if)# security-level 0 ASA2(config-if)# ip add 209.165.201.1 255.255.255.224 ASA2(config-if)# no shut ASA2(config-if)# int e0/1 ASA2(config-if)# nameif inside ASA2(config-if)# security-level 100 ASA2(config-if)# ip add 10.10.1.1 255.255.255.0 ASA2(config-if)# no shut ASA2(config-if)# exit ASA2(config)# nat (inside) 1 0 0 ASA2(config)# global (outside) 1 interface ASA2(config)# route outside 0 0 209.165.201.2 ASA2(config)# policy-map global_policy ASA2(config-pmap)# class inspection_default ASA2(config-pmap-c)# inspect icmp //默认ASA不监控ICMP流量,在此外加上可以使内网ping通外网 ASA2(config-pmap-c)# end ASA2# wr //1、启用ISAKMP ASA2(config)# crypto isakmp enable outside //2、创建ISAKMP策略 ASA2(config)# crypto isakmp policy 1 ASA2(config-isakmp-policy)# encryption aes-256 ASA2(config-isakmp-policy)# hash sha ASA2(config-isakmp-policy)# group 5 ASA2(config-isakmp-policy)# lifetime 86400 ASA2(config-isakmp-policy)# exit //3、创建隧道组 ASA2(config)# tunnel-group 209.165.200.225 type ipsec-l2l ASA2(config)# tunnel-group 209.165.200.225 ipsec-attributes ASA2(config-tunnel-ipsec)# pre-shared-key cisco123 ASA2(config-tunnel-ipsec)# exit ASA2(config)# tunnel-group 209.165.202.129 type ipsec-l2l ASA2(config)# tunnel-group 209.165.202.129 ipsec-attributes ASA2(config-tunnel-ipsec)# pre-shared-key cisco123 ASA2(config-tunnel-ipsec)# exit //4、定义IPSec策略 ASA2(config)# crypto ipsec transform-set AES-SHA esp-aes-256 esp-sha-hmac //5、创建加密映射集 ASA2(config)# access-list outside_cryptomap_1 remark To Encrypto Traffic from 10.10.1.0/24 to 192.168.1.0/24 ASA2(config)# access-list outside_cryptomap_1 extended permit ip 10.10.1.0 255.255.255.0 192.168.1.0 255.255.255.0 ASA2(config)# access-list outside_cryptomap_2 remark To Encrypto Traffic from 10.10.1.0/24 to 172.16.1.0/24 ASA2(config)# access-list outside_cryptomap_2 extended permit ip 10.10.1.0 255.255.255.0 172.16.1.0 255.255.255.0 ASA2(config)# crypto map outside_map 1 match address outside_cryptomap_1 ASA2(config)# crypto map outside_map 1 set transform-set AES-SHA ASA2(config)# crypto map outside_map 1 set peer 209.165.200.225 ASA2(config)# crypto map outside_map 1 set reverse-route ASA2(config)# crypto map outside_map 2 match address outside_cryptomap_2 ASA2(config)# crypto map outside_map 2 set transform-set AES-SHA ASA2(config)# crypto map outside_map 2 set peer 209.165.202.129 ASA2(config)# crypto map outside_map 2 set reverse-route ASA2(config)# crypto map outside_map interface outside //6、启用OSPF动态路由并向内网路由器重新发布路由 ASA2(config)# router ospf 100 ASA2(config-router)# network 10.10.1.0 255.255.255.0 area 0 ASA2(config-router)# area 0 ASA2(config-router)# redistribute static subnets //将子网静态路由重发布到OSPF网络 ASA2(config-router)# exit //7、绕过NAT,为穿越VPN隧道的流量建立NAT豁免规则 ASA2(config)# access-list inside_nat0_outbound remark To Bypass NAT from 10.10.1.0/24 to 192.168.1.0/24 ASA2(config)# access-list inside_nat0_outbound extended permit ip 10.10.1.0 255.255.255.0 192.168.1.0 255.255.255.0 ASA2(config)# access-list inside_nat0_outbound remark To Bypass NAT from 10.10.1.0/24 to 172.16.1.0/24 ASA2(config)# access-list inside_nat0_outbound extended permit ip 10.10.1.0 255.255.255.0 172.16.1.0 255.255.255.0 ASA2(config)# nat (inside) 0 access-list inside_nat0_outbound ASA2(config)# wr
ASA3:
ciscoasa>en ciscoasa# conf t //基本配置部分 ciscoasa(config)# hostname ASA3 ASA3(config)# int e0/0 ASA3(config-if)# nameif outside ASA3(config-if)# security-level 0 ASA3(config-if)# ip add 209.165.202.129 255.255.255.224 ASA3(config-if)# no shut ASA3(config-if)# int e0/1 ASA3(config-if)# nameif inside ASA3(config-if)# security-level 100 ASA3(config-if)# ip add 172.16.1.1 255.255.255.0 ASA3(config-if)# no shut ASA3(config-if)# exit ASA3(config)# nat (inside) 1 0 0 ASA3(config)# global (outside) 1 interface ASA3(config)# route outside 0 0 209.165.202.130 ASA3(config)# policy-map global_policy ASA3(config-pmap)# class inspection_default ASA3(config-pmap-c)# inspect icmp //默认ASA不监控ICMP流量,在此外加上可以使内网ping通外网 ASA3(config-pmap-c)# end ASA3# config t //IPSec配置脚本: crypto isakmp enable outside crypto isakmp policy 1 encryption aes-256 hash sha group 5 authentication pre-share lifetime 86400 exit tunnel-group 209.165.200.225 type ipsec-l2l tunnel-group 209.165.200.225 ipsec-attributes pre-shared-key cisco123 exit tunnel-group 209.165.201.1 type ipsec-l2l tunnel-group 209.165.201.1 ipsec-attributes pre-shared-key cisco123 exit crypto ipsec transform-set AES-SHA esp-aes-256 esp-sha-hmac access-list outside_cryptomap_1 remark TO Encrypt Traffic from 172.16.1.0/24 to 192.168.1.0/24 access-list outside_cryptomap_1 extended permit ip 172.16.1.0 255.255.255.0 192.168.1.0 255.255.255.0 access-list outside_cryptomap_2 remark To Encrypt Traffic from 172.16.1.0/24 to 10.10.1.0/24 access-list outside_cryptomap_2 extended permit ip 172.16.1.0 255.255.255.0 10.10.1.0 255.255.255.0 crypto map outside_map 1 match address outside_cryptomap_1 crypto map outside_map 1 set transform-set AES-SHA crypto map outside_map 1 set peer 209.165.200.225 crypto map outside_map 1 set reverse-route crypto map outside_map 2 match address outside_cryptomap_2 crypto map outside_map 2 set transform-set AES-SHA crypto map outside_map 2 set peer 209.165.201.1 crypto map outside_map 2 set reverse-route crypto map outside_map interface outside router ospf 100 area 0 network 172.16.0.0 255.255.0.0 area 0 redistribute static subnets exit access-list inside_nat0_outbound remark To Bypass NAT from 172.16.1.0/24 to 192.168.1.0/24 access-list inside_nat0_outbound extended permit ip 172.16.1.0 255.255.255.0 192.168.1.0 255.255.255.0 access-list inside_nat0_outbound remark To Bypass from 172.16.1.0/24 to 10.10.1.0/24 access-list inside_nat0_outbound extended permit ip 172.16.1.0 255.255.255.0 10.10.1.0 255.255.255.0 nat (inside) 0 access-list inside_nat0_outbound wr
R1:
conf t int f0/0 ip add 192.168.1.2 255.255.255.0 no shut exit int loopback 0 ip address 192.168.2.1 255.255.255.0 no shutdown exit ip route 0.0.0.0 0.0.0.0 192.168.1.1 router ospf 100 network 192.168.0.0 255.255.0.0 area 0 end wr
R2:
conf t int f0/0 ip add 10.10.1.2 255.255.255.0 no shut exit int loopback 0 ip add 10.10.2.1 255.255.255.255 no shut exit router ospf 100 network 10.10.0.0 255.255.0.0 area 0 exit ip route 0.0.0.0 0.0.0.0 10.10.1.1 end wr
R3:
conf t int f0/0 ip add 172.16.1.2 255.255.255.0 no shut exit int loopback 0 ip add 172.16.2.1 255.255.255.255 no shut exit router ospf 100 network 172.16.0.0 255.255.0.0 area 0 exit ip route 0.0.0.0 0.0.0.0 172.16.1.1 end wr
ISP:
conf t int e0/0 ip add 209.165.200.227 255.255.255.224 no shut int e0/1 ip add 209.165.201.2 255.255.255.224 no shut int e0/2 ip add 209.165.202.130 255.255.255.224 no shut int loopback 0 ip address 1.0.0.1 255.255.255.255 no shut exit ip http server line vty 0 4 no login exit enable password cisco end wr
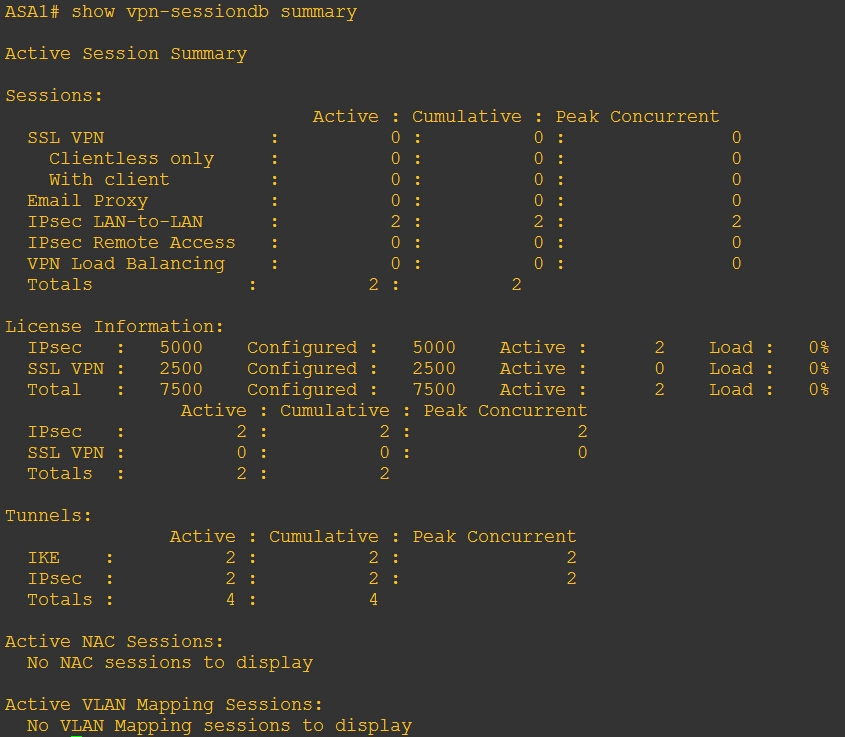
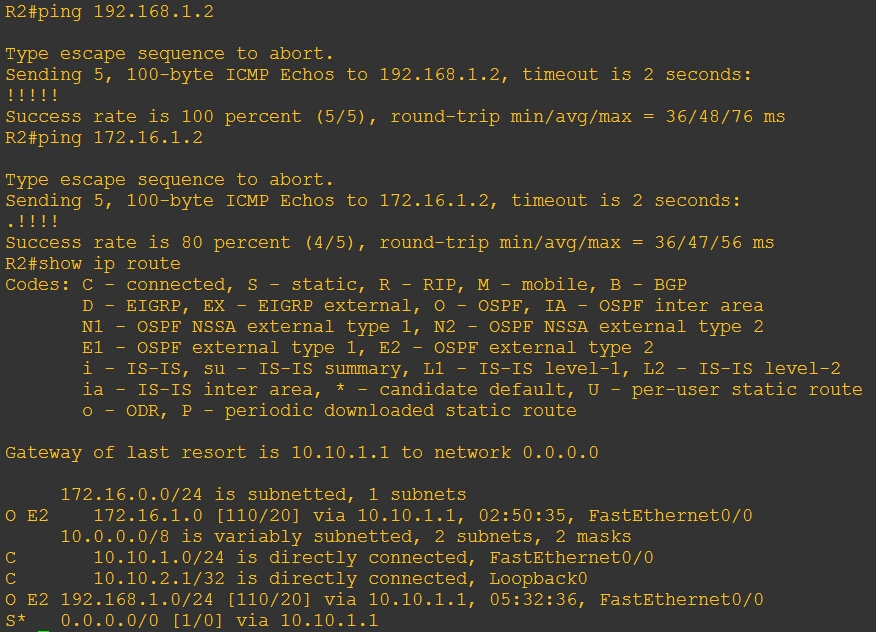
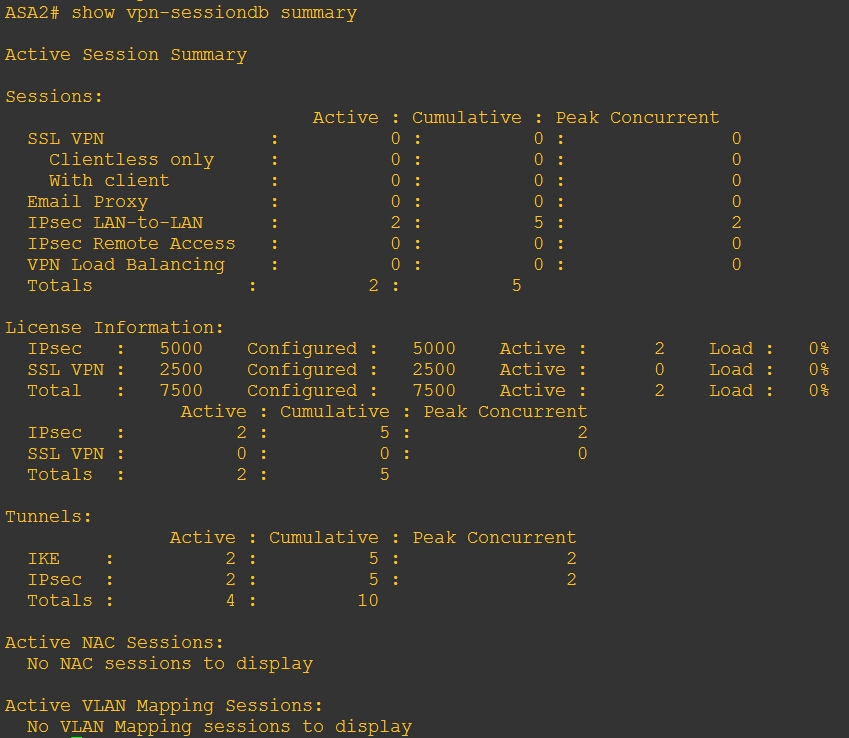
验证:
提示:
1、反向路由注入(RRI)是一种利用路由协议,将远端网络信息分发到本地网络的技术。通过使用RRI,Cisco ASA可以自动将穿越隧道的远端私有网络以静态路由的方式添加到其路由表中,然后使用OSPF将这些路由宣告给本地私有网络中的邻居。
2、隧道组(Tunnel-group)也称为连接配置文件,它定义了一个站点到站点隧道或远程防问隧道,并用来映射分配给指定IPSec对等体的属性。远程访问连接配置文件用于终结所有类型的远程访问VPN隧道,比如IPSec、IPSec上的L2TP和SSL VPN。对于站点到站点IPSec隧道来说,应该使用远端VPN设备的IP地址作为隧道组的名称。对于那些IP地址没有被定义为隧道组的IPSec设备来说,若两个设备的预共享密钥相匹配,那么安全设备就会尝试将远端设备映射到称为DefaultL2LGroup的默认站点到站点组中。
3、对于加密/转换变换集(Crypto Transform Sets)定义了用于传输数据包的加密类型和散列算法类型。它提供了数据认证、机密性和完整性的功能。IPsec转换集会在快速模式中进行协商。Cisco ASA只支持以ESP作为封装协议,并不支持AH。
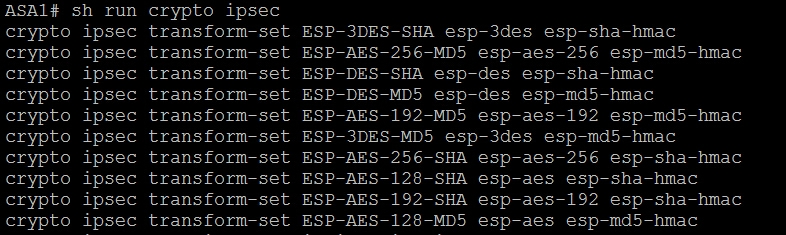
Cisco ASA默认提供了10个加密变换集,也可以直接调用而不自己额外定义,如下图:
加密变换集只本地有效。在变换集中定义了加密(Encryption)算法、散列(Hash)算法及模式(Mode)。其中在加密中Cisco ASA会使用一个专用的硬件加速器来执行IKE请求,使用效强(如AES 256比特)的加密和使用较弱的加密算法(如DES)对于性能的影响几乎相同,所以建议使用效强的加密算法。在散列算法中可以选择SHA-1、MD5和空,建议使用SHA-1,因为它比MD5更加安全。模式是一种封闭模式,可以选择传输模式或隧道模式。传输模式用于加密和认证源于VPN对等体的数据包,隧道模式用于加密和认证源于VPN设备所连主机的IP数据包。
本文出自 “银凯的博客” 博客,请务必保留此出处http://yinkai.blog.51cto.com/3813923/1565152
郑重声明:本站内容如果来自互联网及其他传播媒体,其版权均属原媒体及文章作者所有。转载目的在于传递更多信息及用于网络分享,并不代表本站赞同其观点和对其真实性负责,也不构成任何其他建议。